Installation and Configuration of Active Directory Base Model Banking & Security Solution by Windows Server 2003 through the Act of Central Bank.
1.1 Beginning the Installation Windows Server 2003
Setup creates the disk partitions on the computer running Windows Server 2003, formats the drive, and then copies installation files from the CD to the server.
Note: These instructions assume that installing Windows Server 2003 on a computer that is not already running Windows. If upgrading from an older version of Windows, some of the installation steps may differ.
1.2 To begin the installation
1. Insert the Windows Server 2003 CD in the CD-ROM drive.
2. Restart the computer. If prompted, press any key to boot from the CD.
3. The Windows Server 2003 installation begins.
4. On the Welcome to Setup screen, press Enter.
5. Review and, if acceptable, agree to the license agreement by pressing F8.
6. Follow the instructions to delete all existing disk partitions. The exact steps will differ based on the number and type of partitions already on the computer. Continue to delete partitions until all disk space is labeled as Unpartitioned space.
7. When all disk space is labeled as Unpartitioned space, press C to create a partition in the unpartitioned space on the first disk drive (as applicable).
8. If the server has a single disk drive, split the available disk space in half to create two equal-sized partitions. Delete the total space default value. Type the value of half total disk space at the Create partition of size (in MB) prompt, and the press Enter. After the New partition is created, press Enter.
9. Select Format the partition using the NTFS file system , and then press Enter.
Windows Server 2003 Setup formats the partition and then copies the files from the Windows Server 2003 Server CD to the hard drive. The computer restarts and the Windows Server 2003 Installation Program continues.
1.3 Completing the Installation
To continue the installation with the Windows Server 2003 Setup Wizard
1. The Windows Server 2003 Setup Wizard detects and installs devices. This can take several minutes, and during the process the screen may flicker.
2. In the Regional and Language Options dialog box, make changes required for locale (Here select +6 GMT Astana Dhaka) and then click Next.
3. In the Personalize Your Software dialog, type Moni in the Name box and type Personal in the Organization box. Click Next.
4. Type the Product Key (found on the back of your Windows Server 2003 CD case) in the text boxes provided, and then click Next.
5. In the Licensing Modes dialog box, select the appropriate licensing mode for organization, and then click Next.
6. In the Computer Name and Administrator Password dialog box, type the new computer name DC-1 in the computer name box, and then click Next.
Best Practice: To facilitate the steps in these guides, the Administrator password is left blank and there is no password. This is not an acceptable security practice. When installing a server for the production network, a password should always be set. Windows Server 2003 requires complex passwords by default.
7. When prompted by Windows Setup, click Yes to confirm a blank Administrator password.
8. In the Date and Time Settings dialog box, correct the current date and time if necessary, and then click Next.
9. In the Networking Settings dialog box, make sure Typical Settings is selected, and then click Next.
10. In the Workgroups or Computer Domain dialog box (No is selected by default), click Next.
Note: A domain name could be specified at this point, but this guide uses the Configure Your Server Wizard to create the domain name at a later time.
The Windows Server 2003 Installation continues and configures the necessary components. This may take a few minutes.
11. The server restarts and the operating system loads from the hard drive.
1.4 Preparing a Secondary Partition or Secondary Disk Drive
The unpartitioned space from the installation of Windows Server 2003 requires formatting before it can be accessed by the operating system. Management of disks and partitions occurs through the Computer Management snap-in for Microsoft Management Console. The following steps assume a second disk drive is in use; modify procedures accordingly for a second partition.
To prepare a secondary partition or disk drive
Warning: Formatting a partition destroys all data on that partition. Make sure that select the correct partition.
1. Press Ctrl+Alt+Del and log on to the server as administrator. Leave the password blank.
2. Click the Start button, point to Administrative Tools, and then click Computer Management.
3. To define and format the unpartitioned space, click Disk Management.
4. Right-click Unallocated on Disk 1.
5. To define a partition, click New Partition, and then click Next to continue.
6. Select Primary Partition (default), and then click Next to continue.
7. Click Next leaving the Partition size in MB set to the default.
8. For Assign the following drive letter, select (D….), and then click Next to continue.
9. Under Format this partition with the following settings, click Perform a quick format. Click Next, and then Finish to complete the configuration of the secondary disk drive. Once finished, disk allocation should look similar to the following Figure.
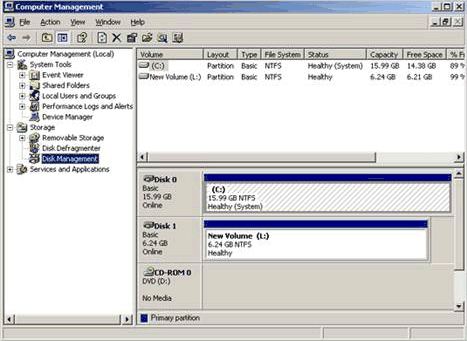
10. Close the Computer Management console.
2.1 How to Install Active Directory on Windows Server 2003
This topic explains how to install Active Directory on a Windows Server 2003.
Before Begin
Either at the console or through a terminal session, we have to log on to as a member of the Administrators group.
Procedure
To install Active Directory on Windows Server 2003
1. Click Start, click Run, type dcpromo, and then click OK
2. On the first page of the Active Directory Installation Wizard, click Next
3. On the next page of the Active Directory Installation Wizard, click Next
4. On the Domain Controller Type page, click Domain Controller for a new domain, and then click Next
5. On the Create New Domain page, click Domain in a new forest, and then click Next
6. On the New Domain Name page, in the Full DNS name for new domain box, type securesystem.com (Domain name), and then click Next.
7. On the Database and Log Folders page, accept the defaults in the Database folder box and the Log folder box, and then click Next
8. On the Shared System Volume page, accept the default in the Folder location box, and then click Next
9. On the DNS Registration Diagnostics page, click Install and configure the DNS server on this computer and set this computer to use this DNS server as its preferred DNS Server, and then click Next
10. On the Permissions page, click Permissions compatible only with Windows 2000 or Windows Server 2003 operating systems, and then click Next
11. On the Directory Services Restore Mode Administrator Password page, enter a password in the Restore Mode Password box, retype the password to confirm it in the Confirm password box, and then click Next
12. On the Summary page, confirm the information is correct, and then click Next
13. When prompted to restart the computer, click Restart now
14. After the computer restarts, log on to as a member of the Administrators group
2.2 Create a new child domain
To create a new child domain
1. Click Start, click Run, and then type dcpromo to start the Active Directory Installation Wizard.
2. On the Operating System Compatibility page, read the information and then click Next. If this is the first time one have installed Active Directory on a server running Windows Server 2003.
3. On the Domain Controller Type page, click Domain controller for a new domain, and then click Next
4. On the Create New Domain page, click Child domain in an existing domain tree, and then click Next
5. On the Network Credentials page, type the user name, password, and user domain of the user account one want to use for this operation, and then click Next. The user account must be a member of the Enterprise Admins group.
6. On the Child Domain Installation page, verify the parent domain and type the new child domain name, and then click Next
7. On the NetBIOS Domain Name page, verify the NetBIOS name, and click Next
8. On the Database and Log Folders page, type the location in which one want to install the database and log folders, or click Browse to choose a location, and then click Next
9. On the Shared System Volume page, type the location in which one want to install the Sysvol folder, or click Browse to choose a location, and then click Next
10. On the DNS Registration Diagnostics page, verify the DNS configuration settings are accurate, and then click Next
11. On the Permissions page select Permissions compatible only with Windows 2000 or Windows Server 2003 operating systems and then click next
12. On the Directory Services Restore Mode Administrator Password page, type and confirm the password that one want to assign to the Administrator account for this server, and then click Next. Use this password when starting the computer in Directory Services Restore Mode
13. Review the Summary page, and then click Next to begin the installation.
14. Restart the computer.
2.3 Setting Up Additional Domain Controllers
2.3.1 Creating Additional Domain Controllers
The following steps should be performed on a computer that has Windows Server 2003 installed and is connected to the common network infrastructure created in Prerequisites in this guide.
Best Practice: While not strictly required, Microsoft highly recommends that all domain controllers, DNS and Dynamic Host Configuration Protocol (DHCP) servers, routers, and printers within the common infrastructure be assigned static Internet Protocol (IP) addresses.
2.3.2 Configuring Static IP addresses
1. Log on to the server.
2. Click the Start button, right-click My Network Places, and then click Properties.
3. Right-click Local Area Connection, and then click Properties.
4. In the Local Area Connection dialog box, double-click Internet Protocol.
5. Select Use the following IP address, and enter the following:
Parameter Computer Name IP Address Subnet Mask Default Gateway DNS Server
Child DomainDC Hpc 192.168.1.3 255.255.255.0 192.168.1.1 192.168.1.1
Replication Partner Dalimpc 192.168.0.3 255.255.255.0 192.168.0.1 192.168.0.1
6. In the Local Area Connection dialog box, click OK.
7. Close the Network and Dial-up Connection dialog box.
2.3.3 Configuring a Replication Partner
The Role of Sites in Active Directory Replication
Sites enable the replication of directory data both within and among sites. Active Directory replicates information within a site more frequently than across sites, implying that better connected domain controllers receive updates first. The domain controllers in other sites will receive all updates to the directory, although, to reduce the bandwidth requirements for slower network connections, updates are scheduled to occur less frequently.
A site is delimited by a subnet and is usually geographically bound. Sites differ in concept from Windows Server 2003 based domains in that sites can span multiple domains, and a domain can span multiple sites. Sites are not part of the domain namespace but they do control replication of domain information and help determine resource proximity. For example, a workstation will select a domain controller within its site against which to authenticate.
Directory information can be exchanged using the following replication transports: Remote Procedure Call (RPC) over Transmission Control Protocol/Internet Protocol (TCP/IP) and Simple Mail Transfer Protocol (SMTP). To take advantage of multi-master replication, one can set up another domain controller to serve as a replication partner for the first domain controller in the Banani child domain.
2.3.4 Configuring an Additional Domain Controller as a Replication Partner
To configure an additional domain controller as a replication partner
1. On dalimpc the Start button, click Run, type DCPromo, and then click OK.
2. Once the Active Directory Installation Wizard appears, click Next to begin.
3. Review the Operating System Compatibility information, and then click Next to continue.
4. On the Domain Controller Type page, select Additional domain controller for an existing domain, and then click Next to continue with the installation of Active Directory.
5. In the Network Credentials box, enter the user name as Administrator, do not enter a password, type the domain name as securesystem.com, and then click Next
6. On the Additional Domain Controller page, enter the domain name as support.securesystem.com, and then click Next to continue.
7. In the NetBIOS Domain Name box, accept the default value of SUPPORT, and then click Next
8. On the Database and Log on Locations page, accept the defaults, and then click Next
9. On the Shared System Volume page, accept the defaults, and then click Next
10. On the Directory Services Restore Mode Administrator Password page, type password for Restore Mode Password and Confirm password. Click Next to continue.
11. Confirm one’s selections on the Summary page, and then click Next to start the configuration of Active Directory
12. Once the Active Directory Installation Wizard completes, click Finish, and then click Restart Now to reboot the system.
3.1 How To Install and Configure DNS Server in Windows Server 2003
This step-by-step process describes how to install and configure DNS on Windows Server 2003 computer.
3.1.1 Before Start
Before start to configure DNS, we have to gather some basic information. Internic must approve some of this information for use on the Internet, but if one is configuring this server for internal use only, can decide what names and IP addresses to use.
One must have the following information:
• The domain name (approved by Internic).
• The IP address and host name of each server that one want to provide name resolution for.
Before configure the computer as a DNS, verify that the following conditions are true:
• Operating system is configured correctly. In the Windows Server 2003 family, the DNS service depends on the correct configuration of the operating system and its services, such as TCP/IP. If we have a new installation of a Windows Server 2003 operating system, then we can use the default service settings. We do not have to take additional action.
• Have allocated all the available disk space.
• All the existing disk volumes use the NTFS file system. FAT32 volumes are not secure, and they do not support file and folder compression, disk quotas, file encryption, or individual file permissions
3.1.2 Install DNS
1. Open Windows Components Wizard. To do so, use the following steps:
• Click Start, click Control Panel, and then click Add or Remove Programs.
• Click Add/Remove Windows Components.
2. In Components, select the Networking Services check box, and then click Details.
3. In Subcomponents of Networking Services, select the Domain Name System (DNS) check box, click OK, and then click Next
4. If prompted, in Copy files from, type the full path of the distribution files, and then click OK.
3.1.3 Configure DNS
1. Start the Configure Your Server Wizard. To do so, click Start, point to All Programs, point to Administrative Tools, and then click Configure Your Server Wizard.
2. On the Server Role page, click DNS server, and then click Next
3. On the Summary of Selections page, view and confirm the options that have selected. The following items should appear on this page:
• Install DNS
• Run the Configure a DNS Wizard to configure DNS
If the Summary of Selections page lists these two items, click Next. If the Summary of Selections page does not list these two items, click Back to return to the Server Role page, click DNS, and then click Next
4. When the Configure Your Server Wizard installs the DNS service, it first determines whether the IP address for this server is static or is configured automatically. If server is currently configured to obtain its IP address automatically, the Configuring Components page of the Windows Components Wizard prompts to configure this server with a static IP address.
a) In the Local Area Connection Properties dialog box, click Internet Protocol (TCP/IP), and then click Properties.
b) In the Internet Protocols (TCP/IP) Properties dialog box, click Use the following IP address, and then type the static IP address, subnet mask, and default gateway for this server.
c) In Preferred DNS, type the IP address of this server.
d) In Alternate DNS, type the IP address of another internal DNS server, or leave this box blank.
e) When finish setting up the static addresses for DNS, click OK, and then click Close.
5. After click Close, the Configure a DNS Server Wizard starts. In the wizard, follow these steps:
a) On the Select Configuration Action page, select the Create a forward lookup zone check box, and then click Next
b) To specify that this DNS hosts a DNS zone that contains DNS resource records for network resources, on the Primary Server Location page, click This server maintains the zone, and then click Next.
c) On the Zone Name page, in Zone name, specify the name of the DNS zone for network, and then click Next. The name of the zone is the same as the name of the DNS domain for organization or branch office.
d) On the Dynamic Update page, click Allow both nonsecure and secure dynamic updates, and then click Next. This makes sure that the DNS resource records for the resources in network update automatically.
e) On the Forwarders page, click No, it should not forward queries, and then click Next
f) On the Completing the Configure a DNS Wizard page of the Configure a DNS Wizard, one can click Back to change any of the settings. To apply selections, click Finish.
g) After finish the Configure a DNS Wizard, the Configure the Server Wizard displays the This Server is Now a DNS Server page. To review all the changes that made to server in the Configure the Server Wizard or to make sure that a new role was installed successfully, click Configure Your Server log. The Configure Server Wizard log is located at %systemroot%\Debug\Configure Server.log. To close the Configure Your Server Wizard, click Finish.
3.1 Install DHCP (1st process)
1. Open Windows Components Wizard. To do so, use the following steps:
• Click Start, click Control Panel, and then click Add or Remove Programs.
• Click Add/Remove Windows Components.
6. In Components, select the Networking Services check box, and then click Details.
7. In Subcomponents of Networking Services, select the Dynamic Host Configuration Protocol (DHCP) check box, click OK, and then click Next
8. If prompted, in Copy files from, type the full path of the distribution files, and then click OK.
9. And finally click finish.
3.2 Setting up a DHCP Server (2nd process)
This will serve as a step-by-step guide on how to setup a DHCP server.
Installing the DHCP server is made quite easy in Windows 2003. By using the “Manage your server” wizard, one is able to enter the details one require and have the wizard set the basics.
1. Open to “Configure your server” wizard, select the DHCP server option for the list of server roles and press Next, Enter the name and description for scope. (Scope: A scope is a collection of IP addresses for computers on a subnet that use DHCP.)
2. The next window is to define the range of addresses that the scope will distribute across the network and the subnet mask for the IP address. Enter the appropriate details and click next.
3. A window in which must add any exclusion to the range of IP addresses specified in the previous window. In this case, eleven IP’s will be reserved and not distributed amongst the network clients.
4. It is now time to set the lease duration for how long a client can use an IP address assigned to it from this scope. It is recommended to add longer leases for a fixed network (in the office for example) and shorter leases for remote connections or laptop computers. In this example we have set lease duration of twelve hours since the network clients would be a fixed desktop computer in a local office and the usual working time is eight hours.
5. Choosing No will allow configuring these options at a later stage. So, click on the radio button besides Yes, I want to configure these options now.
6. The router, or gateway, IP address may be entered in next. The client computers will then know which router to use.
7. In the following window, the DNS and domain name settings enter. The DNS server IP address will be distributed by the DHCP server and given to the client.
8. If one have WINS setup then here is where to enter the IP Address of the WINS server. One can just input the server name into the appropriate box and press “Resolve” to allow it to find the IP address itself. In our case we have not configure WINS server that’s why it is retain empty.
9. The last step is to activate the scope – just presses next when see the window below. The DHCP server will not work unless do this.
10. The DHCP server has now been installed with the basic settings in place. The next stage is to configure it to the needs of network structure.
3.3 Configuring a DHCP server
Here under is a simple explanation of how to configure a DHCP server.
1. The address pool displays a list of IP ranges assigned for distribution and IP address exclusions. We are able to add exclusion by right clicking the address pool text on the left hand side of the mmc window and selecting “new exclusion range”. This will bring up a window (as seen below) which will allow us to enter an address range to be added. Entering only the start IP will add a single IP address.
2. DHCP servers permit to reserve an IP address for a client. This means that the specific network client will have the same IP for as long as wanted it to. To do this we will have to know the physical address (MAC) of each network card.
3. Enter the reservation name, desired IP address, MAC address and description – choose whether want to support DHCP or BOOTP and press add. The new reservation will be added to the list. As an example, we have reserved an IP address (192.168.0.115) for a client computer called Moni.
4. If one right click scope options and press “configure options” one will be taken to a window in which configure more servers and their parameters. These settings will be distributed by the DHCP server along with the IP address. Server options act as a default for all the scopes in the DHCP server. However, scope options take preference over server options.
5. In our opinion, the DHCP server in Windows 2003 is excellent! It has been improved from the Windows 2000 version and is classified as essential for large networks. Imagine having to configure each and every client manually – it would take up a lot of time and require far more troubleshooting if a problem was to arise. Before touching any settings related to DHCP, it is best to make a plan of our network and think about the range of IPs to use for the computers.
4.1 Step-by-Step Guide to Managing Active Directory
Guide Requirements
• Must be logged on as a user with administrative privileges to perform the procedures in this document.
• If working on a domain controller, the Active Directory Schema snap-in might not be installed. To install it:
• At a command-line prompt, type regsvr32 schmmgmt.dll
The Active Directory Schema management snap-in will now be available within MMC.
• On Windows Server 2003–based stand-alone servers or Windows XP Professional workstations, Active Directory Administrative Tools are optional. You can install them from Add/Remove Programs in the Control Panel using the Windows Components wizard or from the ADMINPAK on the Windows Server 2003 CD.
4.2 Using Active Directory Domains and Trusts Snap-In
The Active Directory Domains and Trusts snap-in provides a graphical view of all domain trees in the forest. Using this tool, an administrator can manage each of the domains in the forest, manage trust relationships between domains, configure the mode of operation for each domain (native or mixed mode), and configure the alternative User Principal Name (UPN) suffixes for the forest.
Starting the Active Directory Domains and Trusts Snap-In
To start the snap-in
1. On mpc, click the Start button, point to All Programs, point to Administrative Tools, and then click Active Directory Domains and Trusts. The Active Directory Domains and Trusts snap-in appears as in Figure.
The User Principal Name (UPN) provides an easy-to-use naming style for users to log on to Active Directory. The style of the UPN is based on Internet standard RFC 822, which is sometimes referred to as a mail address. The default UPN suffix is the forest DNS name, which is the DNS name of the first domain in the first tree of the forest. In this guide and the other step-by-step guides in this series, the default UPN suffix is securesystem.com.
One can add alternate UPN suffixes, which increase logon security. One can also simplify user logon names by providing a single UPN suffix for all users. The UPN suffix is only used within the Windows Server 2003 domain and is not required to be a valid DNS domain name.
To add additional UPN suffixes
1. Select Active Directory Domains and Trusts in the upper left pane, right-click it, and then click Properties.
2. Enter any preferred alternate UPN suffixes in the Alternate UPN Suffixes box and click Add.
3. Click OK to close the window.
4.3 Changing Domain and Forest Functionality
Domain and forest functionality, introduced in Windows Server 2003 Active Directory, provides a way to enable domain– or forest-wide Active Directory features within your network environment. Different levels of domain functionality and forest functionality are available depending on your environment.
If all domain controllers in your domain or forest are running Windows Server 2003 and the functional level is set to Windows Server 2003, all domain– and forest-wide features are available. When Windows NT® 4.0 or Windows 2000 domain controllers are included in your domain or forest with domain controllers running Windows Server 2003, only a subset of Active Directory domain– and forest-wide features are available.
The concept of enabling additional functionality in Active Directory exists in Windows 2000 with mixed and native modes. Mixed-mode domains can contain Windows NT 4.0 backup domain controllers and cannot use Universal security groups, group nesting, and security ID (SID) history capabilities. When the domain is set to native mode, Universal security groups, group nesting, and SID history capabilities are available. Domain controllers running Windows 2000 Server are not aware of domain and forest functionality.
Warning: Once the domain functional level has been raised, domain controllers running earlier operating systems cannot be introduced into the domain. For example, if you raise the domain functional level to Windows Server 2003, domain controllers running Windows 2000 Server cannot be added to that domain.
Domain functionality enables features that will affect the entire domain and that domain only. Four domain functional levels are available: Windows 2000 mixed (default), Windows 2000 native, Windows Server 2003 interim, and Windows Server 2003. By default, domains operate at the Windows 2000 mixed functional level.
To raise domain functionality
1. Right-click the domain object (in the example, contoso.com), and then click Raise Domain Functional Level.
2. From the Select an available domain functional level drop-down list, select Windows Server 2003, and then click Raise.
3. Click OK on the warning message to raise domain functionality. Click OK again to complete the process.
4. Close the Active Directory Domains and Trusts window.
4.4 Using the Active Directory Users and Computers Snap-In
To start the Active Directory Users and Computers snap-in
1. Click the Start button, point to All Programs, point to Administrative Tools, and then click Active Directory Users and Computers.
2. Expand Contoso.com by clicking +.
Figure displays the key components of the Active Directory Users and Computers snap-in.
5.1 Recognizing Active Directory Objects
The objects described in the following table are created during the installation of Active Directory.
Icon Folder Description
Domain The root node of the snap-in represents the domain being administered.
Computers Contains all Windows NT, Windows 2000, Windows XP, and Windows Server 2003–based computers that join a domain. This includes computers running Windows NT versions 3.51 and 4.0. If we upgrade from a previous version, Active Directory migrates the machine account to this folder. We can move these objects.
System Contains Active Directory systems and services information.
Users Contains all the users in the domain. In an upgrade, all users from the previous domain will be migrated. Like computers, the user objects can be moved.
We can use Active Directory to create the following objects.
Icon Object Description
User A user object is an object that is a security principal in the directory. A user can log on to the network with these credentials, and access permissions can be granted to users.
Contact A contact object is an account that does not have any security permissions. One cannot log on to the network as a contact. Contacts are typically used to represent external users for the purpose of e-mail.
Computer An object that represents a computer on the network. For Windows NT–based workstations and servers, this is the machine account.
Organizational Unit Organizational units (OUs) are used as containers to logically organize directory objects such as users, groups, and computers in much the same way that folders are used to organize files on your hard disk.
Group Groups can have users, computers, and other groups. Groups simplify the management of large numbers of objects.
Shared Folder A shared Folder is a network share that has been published in the directory.
Shared printer A shared printer is a network printer that has been published in the directory.
6.1 Adding an Organizational Unit
This procedure creates an additional OU in the securesystem domain. Note that we can create nested OUs, and there is no limit to the nesting levels.
These steps follow the Active Directory structure established in the common infrastructure step-by-step guides. If we did not create that structure, add the OUs and users directly under securesystem.com; that is, where Accounts is referred to in the procedure, substitute securesystem.com.
To add an OU
1. Click the + next to Accounts to expand it.
2. Right-click Accounts.
3. Point to New and click Organizational Unit. Type Management as the name of our new organizational unit, and then click OK.
Repeat the previous steps to create additional OUs as follows:
• Organizational unit IT under Accounts.
• Organizational unit Management under Accounts.
• Organizational unit Consumer under the Management organizational unit. (To do this, right-click Management, point to New, and then click Organizational Unit.)
• Organizational units Corporate and Government under the Management organizational unit. Click Management so that its contents will display in the right pane.
When we are finished, we should have the following hierarchy as shown in Figure.
6.1 Creating a User Account
The following procedure creates the user account Zaman in the IT OU.
To create a user account
1. Right-click the IT organizational unit, point to New, and then click User, or click New User on the snap-in toolbar.
2. Type user information as shown in Figure.
3. Click Next to continue.
4. Type pass#word1 in both the Password and Confirm password boxes, and then click Next.
5. Click Finish to accept the confirmation in the next dialog box.
We have now created an account for Zaman in the IT OU.
6.2 To add additional information about this user
1. Select Construction in the left pane, right-click John Smith in the right pane, and then click Properties.
2. Add more information about the user in the Properties dialog box on the General tab as shown in Figure 5, and then click OK. Click each available tab and review the optional user information that may be defined.
6.3 Moving a User Account
Users can be moved from one OU to another within the same domain or a different domain. For example, in this procedure, John Smith moves from the Construction division to the Engineering division.
To move a user from one OU to another
1. Click the Mr. Zaman user account in the right pane, right-click it, and then click Move.
2. On the Move screen, click + next to Accounts to expand it as shown in Figure.
3. Click the IT OU, and then click OK.
7.1 Adding the Workstation to the Domain
1. Click the Start button, click Control Panel, and then double-click the System icon.
2. Click the Computer Name tab, and then click Change.
3. Verify that the Computer name is HQ-CON-WRK-01, and then click the Domain radio button as shown in Figure.
4. Under Member of, type scuresystem for the Domain, and then click OK.
5. The Domain Username and Password dialog box appears. You must supply an account that has privileges to join the domain. In the Name box, type administrator@securesystem.com and click OK. (No password is required for this step-by-step guide.)
2. When receive the message Welcome to the securesystem domain, the workstation has successfully joined the domain. Click OK.
3. Click OK to reboot the computer, and then click OK to close the System Properties window.
4. When the System Settings Change dialog box appears, click Yes to restart the workstation.
8.1 Creating a Group
To create a group
1. Right-click the Engineering OU, click New, and then click Group.
2. In the New Object – Group dialog box, type Tools for Name.
3. Review the type and scope of groups available in Windows Server 2003 as shown in the following table. Leave the default settings, and then click OK to create the Tools group.
• The Group type indicates whether the group can be used to assign permissions to other network resources, such as files and printers. Both security and distribution groups can be used for e-mail distribution lists.
• The Group scope determines the visibility of the group and what type of objects can be contained within the group.
Scope Visibility May Contain
Domain Local Domain Users, Domain Local, Global, or Universal Groups
Global Forest Users or Global Groups
Universal Forest Users, Global, or Universal Groups
8.2 Adding a User to a Group
To add a user to a group
1. Click the IT OUin the left pane.
2. Right-click the Tools group in the right pane, and then click Properties.
3. Click the Members tab, and then click Add.
4. In the Enter the object names to select text box, type Zaman, and then click OK.
5. On the Tools Properties screen, verify Mr. Zaman is now a member of the Tools Security Group, and then click OK.
Publishing a Shared Folder
To help users find shared folders more easily, we can publish information about shared folders in Active Directory. Any shared network folder, including a Distributed File System (Dfs) folder, can be published in Active Directory. Creating a Shared folder object in the directory does not automatically share the folder. This is a two-step process: we must first share the folder, and then publish it in Active Directory.
To share a folder
1. Use Windows Explorer to create a new folder called IT Specs on one of disk volumes.
2. In Windows Explorer, right-click the IT Specs folder, and then click Properties. Click Sharing, and then click Share this folder.
3. On the IT Specs Properties screen, type ES in the Share name box, and then click OK. Close Windows Explorer once complete.
Note: By default, the built-in Everyone group has permissions to this shared folder. We can change the default permission by clicking the Permissions button.
Publishing the Shared Folder in the Directory
To publish the shared folder in the directory
1. In the Active Directory Users and Computers snap-in, right-click the IT OU, point to New, and then click Shared Folder.
2. On the New Object – Shared Folder screen, type IT Specs in the Name box.
3. In the Network Path name box, type \\mpc.securesystem.com\ES, and click OK.
4. Right-click IT Specs, and then click Properties.
5. Click Keywords. For New Value, type specifications, and then click Add to continue. Click OK twice to finish.
Users may now search Active Directory by share name or keyword to locate this shared resource.
Delegating Control of an Organizational Unit
To delegate control of an OU
1. On mpc, open Active Directory Users and Computers. Our structure should resemble Figure
2. In the left pane, right-click Divisions OU, and then click Delegate control. The Delegation of Control wizard appears.
3. On the Welcome page, click Next.
4. On the Users or Groups page, click Add, click Advanced, and then click Find Now. Scroll to AUAdmins, double-click AUAdmins, and then click OK. Click Next to continue.
5. On the Tasks to Delegate page, click Create a custom task to delegate. (This allows you to delegate control of the entire container.) Click Next.
6. On the Active Directory Object Type page, click This folder, existing objects in this folder, and the creation of new objects in this folder (default), and then click Next.
7. On the Permissions page, click Full Control to delegate complete control. Click Next, and then click Finish.
Verifying the Permissions Granted
We can review the access control settings for the AUAdmins group to verify that permissions have been set appropriately.
To verify the permissions granted
1. In the Active Directory Users and Computers snap-in, on the View menu, click Advanced Features.
2. Navigate to and right-click Autonomous Unit under the Divisions OU, and then click Properties.
3. On the Security tab, click Advanced. On the Permissions tab, note the permission entries that apply to AUAdmins as shown in Figure.
4. Double-click AUAdmins. Full control has been granted for the OU and all its sub-objects indicating that permissions were granted correctly.
5. Close all windows.
Delegating Creation and Deletion of Users
The following steps demonstrate the delegation of specific tasks to an authoritative security group. In this example, the HRTeam—members of the Human Resources Department—need permissions for the creation or deletion of user accounts to facilitate employment operations. This type of delegation represents a secondary level of delegation in that control is assigned on a subset of rights for a specific container. In the previous example, all rights for a specific container were assigned.
To delegate control of specific tasks to the HRTeam
1. In the Active Directory Users and Computers snap-in, click the Divisions OU.
2. Right-click Divisions, and then click Delegate control. The Delegation of Control wizard appears. Click Next.
3. On the Users or Groups page, click Add, click Advanced, and then click Find Now. Scroll to HRTeam, double-click HRTeam, and then click OK. Click Next to continue.
4. On the Tasks to Delegate page, under Delegate the following common tasks, click Create, delete, and manage user accounts—the first option—as shown in Figure. Click Next to continue.
5. On the summary page, review the proposed settings, and then click Finish.
Verifying the Permissions Granted
To verify the permissions granted
1. In the Active Directory Users and Computers snap-in, right-click Divisions, and then click Properties.
2. On the Security tab, click Advanced. As shown in Figure 4, permissions that apply to user objects are detailed, including appropriate permissions for the HRTeam.
3. Double-click the second HRTeam entry (Create/Delete User Objects) and note that the Create User objects and Delete User objects rights have been successfully assigned. Note that these permissions Apply onto this object (Divisions OU) and all child objects. Close all windows.
Delegating Resetting of Passwords for All Users
Expanding the previous example of delegating control for specific tasks, this section details a common IT support operation—resetting passwords. As password resets are one of the most frequent IT support requests, delegating control to a lower tier of IT support can streamline IT operations.
To delegate control of password resets to the HelpDesk group
1. In the Active Directory Users and Computers snap-in, click the Divisions OU.
2. Right-click Divisions, and then click Delegate control. The Delegation of Control wizard appears. Click Next.
3. On the Users or Groups page, click Add, click Advanced, and then click Find Now. Scroll to HelpDesk, double-click HelpDesk, and then click OK. Click Next to continue.
4. On the Tasks to Delegate page, under Delegate the following common tasks, click Reset user passwords and force password change at next logon as shown in Figure. Click Next to continue.
5. On the summary page, review the proposed settings, and then click Finish.
Delegating Control of Custom Tasks
The previous examples detailed varying levels of delegating control on specific Active Directory containers. For the delegation of specific tasks, predefined options were selected for delegation. The Delegation of Control Wizard provides an additional level of granularity allowing for custom-built tasks to be assigned to specific users or groups. In the following section, the HRTeam will be assigned permissions to modify specific user attributes to facilitate general employment operations.
To assign control for creating and deleting a user’s personal information in Active Directory to the HRTeam
5. In the left pane, right-click Divisions OU, and then click Delegate control. The Delegation of Control wizard appears. Click Next.
6. On the Users or Groups page, click Add, click Advanced, and then click Find Now. Scroll to HRTeam, double-click HRTeam, and then click OK. Click Next to continue.
7. On the Tasks to Delegate page, click Create a custom task to delegate. (This allows you to delegate control of the entire container.) Click Next.
8. On the Active Directory Object Type screen, click Only the following objects in the folder.
9. Scroll down to the final entry and select the User Objects check box. At the bottom of the Active Directory Object Type screen, select both Create / Delete selected objects in this folder check boxes. Review your settings as shown in Figure 6, and then click Next to continue.
10. On the Permission page, ensure that General is selected (default). Scroll down and select the Read and write personal information check box as shown in Figure.
Note: Selecting the property-specific check box will provide an additional level of detail at the attribute level. For example, if you only wanted the HRTeam to be able to change a user’s street address, you would select that particular attribute.
11. Click Next to continue.
12. On the summary page, review the proposed settings, and then click Finish.
Group Policy Management Console (GPMC)
Installing and Configuring GPMC
Installing GPMC
Installing GPMC is a simple process that involves running a Windows Installer (.MSI) package.
To install the Group Policy Management Console
1. On server mpc, navigate to the folder containing gpmc.msi, double-click the gpmc.msi package, and then click Next.
2. Click I Agree to accept the End User License Agreement (EULA), and then click Next.
3. Click Finish to complete the installation of GPMC.
When the installation is complete, the Group Policy tab that appeared on the Property pages of sites, domains, and organizational units (OUs) in the Active Directory snap-ins is updated to provide a direct link to GPMC. The functionality that previously existed on the original Group Policy tab is no longer available since all functionality for managing Group Policy is available through GPMC.
To open the GPMC snap-in
1. On server mpc, click the Start button, click Run, type GPMC.msc, and then click OK.
Note: Alternatively, either of the following methods can be used to launch the GPMC.
• Click the Group Policy Management shortcut in the Administrative Tools folder on the Start menu or in the Control Panel.
2. Create a custom MMC console: click the Start button, click Run, type MMC, and then click OK. Point to File, click Add/Remove Snap-in, and then click Add. Click to highlight Group Policy Management, click Add, click Close, and then click OK.
Configuring GPMC for Multiple Forests
Multiple forests can be easily added to the GPMC console tree. By default, we can only add a forest to GPMC if there is a two-way trust with the forest of the user running GPMC. We can optionally enable GPMC to work with only one- way trust or even no trust. Adding an additional forest to the GPMC is accomplished by highlighting Group Policy Management at the tree’s root, selecting Action from the context menu, and then clicking AddForest. Since the sample environment only contains a single forest, performing these steps is beyond the scope of this step-by-step guide.
Note: When adding forests to which have no trust, some functionality will not be available. For example, Group Policy Modeling is not available, and it is not possible to open the Group Policy Object Editor on GPOs in the untrusted forest. The untrusted forest scenario is primarily intended to enable copying GPOs across forests.
Managing Multiple Domains Simultaneously
GPMC supports management of multiple domains at the same time, with each domain grouped by forest in the console. By default, only a single domain is shown in GPMC. When we first start GPMC using either the pre-configured snap-in (gpmc.msc) or a custom MMC console, GPMC displays the domain that contains the user account we used to start GPMC. We can specify domains in each forest that we want to manage using GPMC by adding and removing the domains shown in the console.
Note: We can add externally trusted domains, even if we do not have forest trust with the entire forest. By default, must have two-way trust between the domain want to add and the domain of user object. We can also add domains across a one-way trust by disabling the trust detection feature of GPMC, using the Options dialog box on the View menu. To add externally trusted domains, must first use the AddForest dialog box to add one domain from a forest that contains the externally trusted domains. Once this forest is added, can add any domains in that forest that are trusted by right-clicking the Domains node of the forest, and then clicking Show Domains.
To add the banani.securesystem.com child domain to the console
1. In the Group Policy Management window, click the plus sign (+) next to Forest:securesystem.com to expand the tree, and then click the plus sign (+) next to Domains.
2. Right-click Domains, and then click Show Domains.
3. Select the check box next to banani.securesystem.com as shown in Figure, and then click OK.
In each domain available to GPMC, the same domain controller is used for all operations in that domain. This includes all operations on the GPOs, OUs, security principals, and WMI filters that reside in that domain. In addition, when the Group Policy Object Editor is opened from GPMC, it always uses the same domain controller that is targeted in GPMC for the domain where that GPO is located.
GPMC allows to choose which domain controller to use for each domain. We can choose from these four options.
• Use the primary domain controller (PDC) emulator (default choice).
• Use any available domain controller.
• Use any available domain controller that is running a Windows Server 2003 family operating system. This option is useful if restoring a deleted GPO that contains Group Policy software installation settings.
• Use a specific domain controller that you specify.
To change the domain controller used by GPMC for the banani.securesystem.com domain
1. In the Group Policy Management window, under the Domains folder, right-click banani.securesystem.com, and then click Change Domain Controller.
2. In the Change Domain Controller dialog box, click This domain controller, and then click to highlight hpc.banaini.securesystem.com as shown in Figure.
3. Click OK to continue.
Managing Group Policy Objects
Viewing Domain GPOs
Within each domain, GPMC provides a policy-based view of Active Directory and the components associated with Group Policy, such as GPOs, WMI filters, and GPO links. The view in GPMC is similar to the view in Active Directory Users and Computers MMC snap-in in that it shows the OU hierarchy. However, GPMC differs from this snap-in because instead of showing users, computers, and groups in the OUs, it displays the GPOs that are linked to each container, as well as the GPOs themselves.
Each domain node in GPMC displays the following items.
• All GPOs linked to the domain.
• All top-level OUs and a tree view of nested OUs and GPOs linked to each of the OUs.
• The Group Policy Objects container showing all GPOs in the domain.
• The WMI Filters container showing all WMI filters in the domain.
To view GPOs associated with a particular container
1. Under the Domains tree, click the securesystem.com tree. The GPOs associated with the container (domain root) appear as shown in Figure. This concept can be applied to any domain container.
To view all GPOs associated with a particular domain
• Under the Domains tree, click the plus sign (+) next to securesystem.com, and then click Group Policy Objects.
Searching for GPOs
Searching for GPOs is available at the forest or domain level. Individual or multiple search parameters can assist in narrowing search results within a large set of GPOs.
To find a specific GPO within the contoso.com forest using multiple search parameters
1. In the console tree, right-click Forest:securesystem.com, and then click Search.
2. In the Search item box, select GPO Name, type Password for Value, and then click Add.
3. In the Search item box, select Computer Configuration, select Security for Value, and then click Add.
4. Click Search. The results should appear as shown in Figure.
5. Once the search results are returned, may do one of the following:
• To open the GPO for editing, click Edit.
• To save the search results, click Save results. In the Save GPO Search Results dialog box, specify the file name for the saved results, and then click Save.
• To navigate to a GPO found in the search, double-click the GPO in the search results list.
• To clear the search results, click Clear.
• To close the Search for Group Policy Objects dialog box, click Close.
Scoping GPOs
The value of Group Policy can only be realized through properly applying the GPOs to the Active Directory containers want to manage. Determining which users and computers will receive the settings in a GPO is referred to as “scoping the GPO”. Scoping a GPO is based on three factors.
• The site(s), domain(s), or OU(s) where the GPO is linked The primary mechanism by which the settings in a GPO are applied to users and computers is by linking the GPO to a site, domain, or OU in Active Directory. The location where a GPO is linked is referred to as the Scope of Management or SOM (also seen as SDOU in previous white papers). There are three types of SOMs: sites, domains, and OUs. A GPO can be linked to multiple SOMs, and an SOM can have multiple GPOs linked to it. A GPO must be linked to an SOM for it to be applied.
• The security filtering on the GPO By default all Authenticated Users that are located in the SOM (and its children) where a GPO is linked will apply the settings in the GPO. We can further refine which users and computers will receive the settings in a GPO by managing permissions on the GPO. This is known as security filtering. For a GPO to apply to a given user or computer, that user or computer must have both Read and Apply Group Policy permissions on the GPO. By default, GPOs have permissions that allow the Authenticated Users group both of these permissions. This is how all authenticated users receive the settings of a new GPO when it is linked to a SOM (OU, domain, or site). These permissions can be changed, however, to limit the scope of the GPO to a specific set of users, groups, and/or computers within the SOM(s) where it is linked.
• The WMI filter on the GPO WMI filters allow an administrator to dynamically determine the scope of GPOs based on attributes (available through WMI) of the target computer. A WMI filter consists of one or more queries that are evaluated to be either true or false against the WMI repository of the target computer. The WMI filter is a separate object from the GPO in the directory. To apply a WMI filter to a GPO, you link the filter to the GPO. This is shown in the WMI filtering section on the Scope tab of a GPO. Each GPO can have only one WMI filter; however, the same WMI filter can be linked to multiple GPOs. When a GPO that is linked to a WMI filter is applied on the target computer, the filter is evaluated on the target computer. If the WMI filter evaluates to false, the GPO is not applied. If the WMI filter evaluates to true, the GPO is applied.
To scope the Domain Password Policy GPO found in the previous search
1. In the Search for Group Policy Objects search results pane, double-click Domain Password Policy, and then click Close.
Note: Once the Search for Group Policy Objects dialog box is closed, the previously selected GPO will have focus in the GPMC. The GPO Scope page will appear as shown in Figure.
To review the policies that will be applied by a GPO
1. In the Domain Password Policy results pane, click the Settings tab, and then click Show All. A summary of all defined policy settings will appear as shown in Figure. Undefined settings are not displayed.
GPO Policy Inheritance and Link Order
The Group Policy Inheritance tab for a given container shows all GPOs (except for GPOs linked to sites) that would be inherited from parent containers. The precedence column on this tab shows the overall precedence for all the links that would be applied to objects in that container, taking into account both Link Order and the Enforcement attribute of each link, as well as Block Inheritance.
To view policy inheritance on a container
1. In the Group Policy Management window, under the securesystem.com tree, expand the Accounts OU, and then click the Headquarters OU as shown in Figure.
If multiple GPOs are linked to the same container and have settings in common, there must be a mechanism for reconciling the settings. This behavior is controlled by the link order. The lower the link order number, the higher the precedence. Information about the links for a given container is shown on the Linked Group Policy Objects tab of a given container. This pane shows if the link is enforced, if the link is enabled, the status of the GPO, if a WMI filter is applied, when it was modified, and the domain container where it is stored. An administrator or users who have been delegated permissions to link GPOs to the container can change the link order by highlighting a GPO link and using the up and down arrows to move the link higher or lower in the link order list.
To change policy link order on a container
1. On the Headquarter screen, click the Linked Group Policy Objects.
2. Under the GPO column, click Linked Policies, and then click the up arrow just to the left of the Link Order column. When finished, the linking order for GPOs under the Headquarters OU should appear as shown in Figure.
13.1 GPO Backup, Restore, Copy, Import
13.1.1 Backing Up a GPO
Backing up a GPO copies the data in the GPO to the file system. The backup function also serves as the export capability for GPOs. A GPO backup can be used to restore the GPO to the backed-up state, or to import the settings in the backup to another GPO.
Backing up a GPO saves all information that is stored inside the GPO to the file system. This includes the following:
• The GPO globally unique identifier (GUID) and domain GPO settings
• The discretionary access control list (DACL) on the GPO
• The WMI filter link, if there is one, but not the filter itself
• Links to IP Security policies, if any
• Extensible Markup Language (XML) report of the GPO settings, which can be viewed as HTML from within GPMC
• Date and time stamp of the backup
• User-supplied description of the backup
Backing up a GPO only saves data that is stored inside the GPO. Data that is stored outside the GPO includes the following:
• Links to a site, domain, or OU
• WMI filter
• IP Security policy
This data is not available when the backup is restored to the original GPO or imported into a new one.
To backup a Domain Policy GPO
1. In the Group Policy Management window, under the securesystem.com tree, click the Group Policy Objects folder.
2. In the Group Policy Objects folder, right-click the A domain Policy GPO, and then click Back Up.
3. In the Back Up Group Policy Object dialog box, type D:\windows for Location, type Name of the Policy Backup for Description, and then click Back Up.
4. Once the backup is complete, click OK to continue.
Managing Backups
Multiple backups of the same or different GPO can be stored in the same file system location. Each backup is identified by a unique backup ID. The collection of backups in a given file system location can be managed using the Manage Backups dialog box in GPMC or through the scriptable interfaces. The Manage Backups dialog box is available by right-clicking either the Domains node or the Group Policy Objects node in a given domain. When open Manage Backups from the Group Policy Objects node, the view is automatically filtered to show only backups of GPOs from that domain. When opened from the Domains node, the Manage Backups dialog box shows all backups, regardless of which domain they are from.
To manage available GPO backups
1. In the Group Policy Management window, under the securesystem.com tree, right-click the Group Policy Objects folder, and then click Manage Backups. The Manage Backups window should appear as shown in Figure.
2. In the Manage Backups window, click to highlight the Domain Password Policy Backup created previously, and then click View Settings.
3. Review the detailed GPO information, and then close Internet Explorer.
13.1.2 Restoring from Backup
Restoring a GPO re-creates the GPO from the data in the backup. A restore operation can be used in both of the following cases: the GPO was backed up but has since been deleted, or the GPO is live and you want to roll back to a known previous state. A restore operation replaces the following components of a GPO.
• GPO settings
• The DACL on the GPO
• WMI filter links (but not the filters themselves)
The restore operation does not restore objects that are not part of the GPO. This includes links to a site, domain, or OU; WMI filters, and IPSec policies.
To restore the Domain Password Policy GPO
In the Manage Backups window, click Restore.
1. When prompted, click OK to restore the selected backup.
2. Click OK after the GPO restoration is complete.
3. In the Manage Backups dialog box, click Close.
13.2 Copying a GPO
A copy operation allows to transfer settings from an existing GPO in Active Directory directly into a new GPO. The new GPO created during the copy operation is given a new GUID and is unlinked. One can use a copy operation to transfer settings to a new GPO in the same domain, another domain in the same forest, or a domain in another forest. Because a copy operation uses an existing GPO in Active Directory as its source, trust is required between the source and destination domains. Copy operations are suited for moving Group Policy between production environments. They are also used for migrating Group Policy that has been tested in a test domain or forest to a production environment, as long as there is trust between the source and destination domains.
To copy a GPO
1. Under the securesystem.com tree in the Group Policy Objects folder, right-click the Enforced User Policies GPO, and then click Copy.
2. Click the plus sign (+) next to banani.securesystem.com to expand the domain, and then click the plus sign (+) next to Group Policy Objects to expand the tree.
3. Right-click Group Policy Objects, and then click Paste.
4. On the Cross-Domain Copying Wizard, click Next to continue.
5. On the Specify Permissions screen, select Use the default permissions for new GPOs (default) as shown in Figure, and then click Next.
6. Once the original GPO is scanned, click Next to continue.
7. On the Completing the Cross-Domain Copying Wizard screen, verify settings, and then click Finish.
8. Once the copy operation is complete, click OK.
Note: The Enforced User Policies GPO has been copied to the banani.securesystem.com domain; however, it has not been linked to any container.
To link the Enforced User Policies GPO to the root of banani.securesystem.com
• Right-click banani.securesystem.com, click Link an Existing GPO, click to highlight Enforced User Policies, and then click OK.
13.3 Importing a GPO
The import operation transfers settings into an existing GPO in Active Directory using a backed up GPO in the file system location as its source. Import operations can be used to transfer settings from one GPO to another GPO within the same domain, to a GPO in another domain in the same forest, or to a GPO in a domain in a different forest. The import operation always places the backed up settings into an existing GPO. It erases any pre-existing settings in the destination GPO. Import does not require trust between the source domain and destination domain; therefore, it is useful for transferring settings across forests and domains that do not have trust. Importing settings into a GPO does not affect its DACL, links on sites, domains, or OUs to that GPO, or a link to a WMI filter.
To import the securesystem.com Domain Password Policy into banani.securesystem.com Domain Password Policy
1. In the Group Policy Management window, right-click banani.securesystem.com, and then click Create and Link a GPO here.
2. In the New GPO dialog box, type Domain Password Policy for the Name, and then click OK.
3. Under Group Policy Objects in the banani.securesystem.com tree, right-click the Domain Password Policy GPO, and then click Import Settings.
4. On the Import Settings Wizard, click Next to continue.
5. On the Backup GPO screen, click Next to continue without backup as the GPO currently has no policy definitions.
6. Accept the default backup folder, D:\windows, and then click Next to continue.
7. Since the Domain Password Policy is the only current backup, it is selected by default. Click Next to begin importing the settings from this GPO.
8. Click Next after the GPO is scanned for security principals, and then click Finish.
9. When the Import Settings Wizard completes, click OK.
13.4 To verify the banani.securesystem.com Domain Password Policy
1. Under Group Policy Objects in the banani.securesystem.com tree, click Domain Password Policy, and then click Show All in the results pane. The settings should be identical to those shown in Figure.
GPO Modeling
Group Policy Modeling
Group Policy Modeling is a simulation of what would happen under circumstances specified by an administrator. It requires that you have at least one domain controller running Windows Server 2003 because this simulation is performed by a service running on a domain controller that is running Windows Server 2003.
With Group Policy Modeling, you can either simulate the RSoP data that would be applied for an existing configuration, or you can perform “what-if” analyses by simulating hypothetical changes to your directory environment and then calculating the RSoP for that hypothetical configuration. For example, you can simulate changes to security group membership, or changes to the location of the user or computer object in Active Directory. Outside of GPMC, Group Policy Modeling is referred to as RSoP – planning mode.
To simulate the effects of GPOs
1. In the Group Policy Management window, click the minus sign (-) next to Domains to collapse the tree.
2. Under the Forest: securesystem.com tree, right-click Group Policy Modeling, and then click Group Policy Modeling Wizard.
3. On the Group Policy Modeling Wizard screen, click Next.
4. On the Domain Controller Selection screen, leave the default settings, and then click Next.
5. On the User and Computer Selection screen, under User information, click User. Click Browse, type Christine under Enter object name to select, and then click OK. Select the Skip to the final page of this wizard without collecting additional data check box, and then click Next. Your settings should appear as shown in Figure.
6. On the Summary of Selections screen, click Next to start the simulation.
7. Click Finish. The right pane will contain the simulation results.
Group Policy Feature Set
Several administrative tools are available for the management of Group Policy settings including:
• Group Policy Object Editor Microsoft Management Console (MMC) snap-in
• Default MMC snap-in available in Windows Server 2003 and the one used throughout this step-by-step guide.
• Group Policy Management Console (GPMC) with Service Pack 1
• GPMC extends the default Group Policy Object Editor by simplifying the management of Group Policy, making it easier to understand, deploy, manage, and troubleshoot Group Policy implementations. GPMC also enables automation of Group Policy operations via scripting
• Third-party extensions, which host other policy settings
Group Policy includes policy settings for User Configuration, which affect users, and for Computer Configuration, which affect computers.
With Group Policy, you can do the following:
• Manage registry-based policy with Administrative Templates. Group Policy creates a file that contains registry settings that are written to the User or Local Machine portion of the registry database.
• Assign scripts. This includes scripts such as computer startup, shutdown, logon, and logoff.
• Redirect folders. You can redirect folders, such as My Documents and My Pictures, from the Documents and Settings folder on the local computer to network locations.
• Manage applications. You can assign, publish, update, or repair applications by using Group Policy Software Installation.
• Specify security options.
This document presents a brief overview of Group Policy, and shows how to use the Group Policy snap-in to specify policy settings for groups of users and of computers.
15.1 Group Policy and the Microsoft Management Console
Group Policy is directly integrated with Active Directory management tools through the MMC snap-in extension mechanism. The Active Directory snap-ins set the scope of management for Group Policy. The most common way to access Group Policy is by using the Active Directory User and Computers snap-in, for setting the scope of management to domain and OUs. One can also use the Active Directory Sites and Services snap-in to set the scope of management to a site. These two tools can be accessed from the Administrative Tools program group; the Group Policy snap-in extension is enabled in both tools. Alternatively, we can create a custom MMC console, as described in the next section.
Configuring a Custom Console
The examples in this document use the custom MMC console that you can create by following the procedures outlined in this section. We need to create this custom console before attempting the remaining procedures in this document.
To configure a custom console
1. Log on to mpc as administrator@securesystem.com.
2. Click the Start button, click Run, type mmc, and then click OK.
3. In the Console1 window, click File, and then click Add/Remove Snap-in.
4. In the Add/Remove Snap-in dialog box, click Add.
5. In the Add Standalone Snap-in dialog box, in the Available standalone snap-ins list box, click Active directory users and computers, and then click Add.
6. Double-click Active directory sites and services snap-in in the Available standalone snap-ins list box.
7. Scroll down, and then double-click Group Policy Object Editor.
8. In the Select Group Policy Object dialog box, ensure Local computer is selected under Group Policy Object. Click Finish, and then click Close.
9. In the Add/Remove Snap-in dialog box, click the Extensions tab. Ensure that the Add all extensions check box is selected for each primary extension added to the MMC console (these are selected by default). Click OK.
To save console changes
1. In the MMC console, click File, and then click Save.
2. In the Save As dialog box, in the File name text box, type GPWalkThrough, and then click Save. The console should appear as shown in Figure 1.
15.2 Accessing Group Policy
We can use the appropriate Active Directory tools to access Group Policy while focused on any site, domain, or OU.
To open Group Policy from Active Directory Sites and Services
1. In the GPWalkthrough MMC console, in the console tree, click the plus sign (+) next to Active Directory Sites and Services.
2. In the console tree, click the plus sign (+) next to Sites, and then right-click Default-First-Site-Name.
3. Click Properties, and then click the Group Policy tab.
4. Click Cancel.
To open Group Policy from Active Directory Users and Computers
1. In the console tree in the GPWalkthrough MMC console, click the plus sign (+) next to Active Directory Users and Computers.
2. In the console tree, right-click contoso.com to access Group Policy.
3. Click Properties, and then click the Group Policy tab.
4. Click Cancel.
To access Group Policy scoped to a specific computer (or the local computer), we must load the Group Policy snap-in into the MMC console namespace targeted at the specific computer (or local computer). There are two major reasons for these differences:
• Sites, domains, and OUs can have multiple GPOs linked to them; these GPOs require an intermediate property page to manage them.
• A GPO for a specific computer is stored on that computer, and not in Active Directory.
16.1 Creating a Group Policy Object
Group Policy settings are contained in GPOs that are individually linked to selected Active Directory objects, such as sites, domains, or OUs.
To create and link a new GPO to the Headquarters OU
1. In the GPWalkThrough MMC, expand contoso.com under Active Directory Users and Computers.
2. Click the plus sign (+) next to Accounts to expand the tree.
3. Right-click Headquarters, and then click Properties.
4. On the Headquarters Properties page, click the Group Policy tab.
5. Click New, type HQ Policy, and then press Enter. The Headquarters Properties page appears as shown in Figure.
The previous steps showed how to create and automatically link a GPO to an Active Directory container—the Headquarters OU. However, the GPO will have no direct impact on users or computers until its various settings are defined. The next section shows how to edit the HQ Policy GPO settings.
Multiple GPOs may be created and/or linked under any Active Directory container. If more than one GPO is associated with an Active Directory container, we must ensure that the GPOs are ordered correctly. GPOs higher in the list that have the highest precedence are processed last. (This is what gives them a higher precedence.)
GPOs are objects; they have context menus for viewing the properties of each GPO. We can use the context menus to obtain and modify general information about a GPO. This information includes Discretionary Access Control Lists (DACLs), and lists the other site, domain, or OUs to which this GPO is linked.
Best Practice: We can further refine a GPO through user or computer membership in security groups by setting DACLs based on that membership. For information about using DACLs, see the section Security Group Filtering.
17.1 Managing Group Policy
To manage Group Policy
• Access the context menu of a site, domain, or OU
• Select Properties, and then click the Group Policy tab. This displays the Group Policy Properties page.
Note the following for the Group Policy Properties page.
• This page displays any GPOs that have been associated with the currently selected site, domain, or OU. The links are objects; they have a context menu that you can access by right-clicking the object. (Right-clicking the white space displays a context menu for creating a new link, adding a link, or refreshing the list.)
• This page also shows an ordered GPO list, with the highest priority GPO at the top of the list. You can change the list order by selecting a GPO, and then using the Up or Down arrow keys.
• To associate (link) a GPO, click the Add button.
• To edit an existing GPO in the list, select the GPO, and then click the Edit button, or double-click the GPO. This starts the Group Policy Object Editor, where you can modify the GPO. For more information about modifying GPOs, see Editing a Group Policy Object.
• To permanently delete a GPO from the list, select it from the list, and then click the Delete button. When prompted, select Remove the link and delete the Group Policy object permanently. Be careful when deleting a GPO since it may be associated with another site, domain, or OU. If you only want to remove the GPO’s association with the current container, select the GPO from the links list, click Delete, and then, when prompted, select Remove the link from the list.
• To determine what other sites, domains, or OUs are associated with a given GPO, right-click the GPO, select Properties on the context menu, and then click the Links tab on the GPO Properties page. Click Find Now to retrieve a current link list for this GPO.
• By right-clicking the GPO, you can set the No override option. This option marks the selected GPO so that its policies cannot be overridden by another GPO.
Note: We can enable the No Override option on more than one GPO. All GPOs marked as No override will take precedence over all other GPOs that are not marked. Of those GPOs marked as No override, the GPO with the highest priority will be applied after all the other similarly marked GPOs.
• By right-clicking the GPO, you can set the GPO as Disabled, which simply disables (deactivates) the GPO without removing it from the list.
Note: It is also possible to disable only the User or Computer portion of the GPO. To do this, right-click the GPO, click Properties, and then, on the General tab, click either Disable Computer Configuration settings or Disable User Configuration settings.
• On the Active Directory container’s Group Policy properties page, we can set Block policy inheritance to negate all GPOs that exist higher in the hierarchy. However, it cannot block any GPOs that are enforced by using the No override check box; those GPOs will always be applied.
Note: Policy settings contained within the local GPO that are not specifically overridden by domain-based policy settings are also always applied. Block Policy Inheritance at any level will not remove local policy.
17.2 Editing a Group Policy Object
We can use the GPWalkThrough custom console created previously to edit a GPO.
To edit the HQ Policy GPO
1. In the GPWalkThrough MMC console, double-click the HQ Policy GPO (or highlight it, and then click Edit). This opens the Group Policy Object Editor for editing the HQ Policy. It should appear as shown in Figure.
2. Close the Group Policy Object Editor for the HQ Policy.
17.3 Adding or Browsing a Group Policy Object
To add a GPO
1. In the Headquarters Properties page, on the Group Policy tab, click Add. The Add a Group Policy Object Link dialog box lists GPOs currently associated with Domains/OUs, sites, or all GPOs that exist within the Active Directory structure. Figure illustrates this dialog box.
17.4 Review the following components of the Add a Group Policy Object Link dialog box and then close the dialog box.
• The Look in drop-down box allows navigate the entire Active Directory structure in search of a GPO. As change the value in this box, GPOs and all child objects will be displayed in the results pane.
• On the Domains/OUs tab, the list box displays the sub-OUs and GPOs for the currently selected domain or OU. To navigate the hierarchy, double-click a sub-OU or use the Up one level toolbar button.
• On the Sites tab, all GPOs associated with the selected site are displayed. Use the drop-down list to select another site. There is no hierarchy of sites.
• The All tab shows a flat list of all GPOs that are stored in the selected domain. This is useful when you want to select a GPO that you know by name, rather than where it is currently associated. This is also the only place to create a GPO that does not have a link to a site, domain, or OU.
• To create an unlinked GPO on the All tab, select the Create New Group Policy Object toolbar button or right-click the white space, and then click New. Name the new GPO, click Enter, and then click Cancel—do not click OK. Clicking OK links the new GPO to the current site, domain, or OU. Clicking Cancel creates an unlinked GPO.
• To associate a GPO with the currently selected domain or OU, double-click the desired GPO.
18.1 Configuring Administrative Templates
The following steps provide a simple example of using Administrative Templates to remove the Run command from a user’s desktop. One should become familiar with all the available settings offered in the Administrative Templates. Additional step-by-step guides in this series will use settings available in the Administrative Templates.
To set registry-based settings using administrative templates
1. In the Group Policy Object Editor for the HQ Policy GPO, click the plus sign (+) next to the Administrative Templates in the User Configuration node.
2. Click Start Menu & Taskbar. Note that the details pane shows all policies as Not configured.
3. In the right pane, double-click the Remove Run menu from Start menu policy.
4. In the Remove Run menu from Start menu dialog box, click Enabled (as shown in Figure 6). Click OK to finish.
Note the Previous Policy and Next Policy buttons in the dialog box. We can use these buttons to navigate the details pane for setting the state of other policies. We can also leave the dialog box open and click another policy in the details pane of the Group Policy snap-in. After the details pane has the focus, we can use the Up and Down arrow keys on the keyboard and press Enter to quickly browse through the settings (or Explain tabs) for each policy in the selected node.
Note the change in state to Enabled in the Setting column of the details pane. This change is immediate; it has been saved to the GPO. If you are in a replicated domain controller environment, this action sets a flag that triggers a replication cycle.
If one log on to a workstation in the securesystem.com domain with a user from the Headquarters OU, you will note that the Run menu has been removed.
Note: At this point, we may want to experiment with the other available policies. Look at the text in the Explain tab for information about each policy.
19.1 Deploying Scripts Through Group Policy Objects
We can define a GPO setting that runs scripts when users log on or log off, or when the system starts or shuts down. All scripts are Windows Scripting Host (WSH)–enabled. As such, they may include Java Scripts or Microsoft Visual Basic® Scripts, as well as .bat and .cmd files.
Creating a Logon Script
Note: This procedure uses the welcome.bat script. Create an Included Items folder, and then create the file welcome.bat within the Included Items folder by copying the script.
To define a logon script Group Policy setting
1. Close the Group Policy Object Editor for the HO Policy.
2. In the HeadOffice Properties dialog box, click Close.
3. In the GPWalkthrough console, right-click the securesystem.com domain, click Properties, and then click the Group Policy tab.
4. On the Group Policy properties page, select the Default Domain Policy GPO from the Group Policy objects links list, and then click Edit to open the Group Policy Object Editor snap-in.
5. In the Group Policy snap-in, under User Configuration, click the plus sign (+) next to Windows Settings, and then click the Scripts (Logon/Logoff) node.
6. In the details pane, double-click Logon.
The Logon Properties dialog box displays the list of scripts that run when a designated user logs on. This is an ordered list, with the script that is to run first appearing at the top of the list. We can change the order by selecting a script, and then using the Up or Down arrow keys.
To add a new script to the list, click the Add button. This displays the Add a Script dialog box. Browsing from this dialog box allows you to specify the name of an existing script located in the current GPO, or to browse to another location and select it for use in this GPO. The script file must be accessible to the user at logon, or it does not run. Scripts in the current GPO are automatically available to the user. To create a new script, right-click the empty space, select New, and then select a new file.
To edit the name or the parameters of an existing script in the list, select it, and then click the Edit button. This button does not allow the script itself to be edited. To edit the script, use the Show Files button. To remove a script from the list, select it, and then click Remove.
The Show Files button displays a Windows Explorer view of the scripts for the GPO. This allows quick access to these files or to the place to copy support files to if the script files require them. If one changes a script file name from this location, must also use the Edit button to change the file name, or the script cannot execute.
Note: If the View Folder Options for this folder are set to Hide file extensions for known file types, the file may have an unwanted extension that prevents it from being run.
7. Click the Start button, click All Programs, click Accessories, and then click Windows Explorer. Navigate to the welcome2006.bat file in the Included Items directory, right-click the file, and then click Copy.
8. Close Windows Explorer.
9. In the Logon Properties dialog box, click the Show Files button, and paste the welcome.bat script into the default file location. It should appear as shown in Figure.
10. Close the window containing welcome.js.
11. In the Logon Properties dialog box, click Add.
12. In the Add a Script dialog box, click Browse. In the Browse dialog box, double-click the welcome.js file.
13. In the Add a Script dialog box, click OK (no script parameters are needed), and then click OK again.
14. Close the Group Policy Object Editor.
15. On the securesystem.com Properties page, click Cancel.
This script will be immediately available to any member of securesystem.com since it was defined within the Default Domain Policy. We can log on to a client workstation to verify that the script is run when a user logs on.
20.1 Security Group Filtering
We can refine the effects of any GPO on users or computers by stipulating how a selected GPO is applied to security groups. To do this, use the Security tab on the Properties page of a GPO to set DACLs. DACLs are used primarily for performance reasons, although the feature allows for tremendous flexibility in designing and deploying GPOs, and the policies they contain.
By default, GPOs affect all users and machines that are contained in the linked site, domain, or OU. By using DACLs, the effect of any GPO can be modified to exclude or include the members of any security group.
To filter GPO application based on Security Group membership
1. In the GPWalkthrough console, under the Accounts OU, right-click the Headquarters OU, and then click Properties.
2. In the Headquarters Properties dialog box, click the Group Policy tab.
3. Right-click the HQ Policy GPO in the Group Policy Object Links list, and then select Properties from the context menu.
1. On the Properties page, click the Security tab.
4. On the Security property page, click Add.
5. In the Select Users, Computers, and Groups dialog box, type Management in the Enter the object names to select, and then click OK.
6. In the Security tab on the HQ Policy Properties page, select the Management group, and view the permissions.
Note: By default, only the Read Access Control Entry (ACE) is set to Allow for the Management group. This means that the members of the Management group do not have this GPO applied to them unless they are also members of another group (by default, they are also Authenticated Users) that has the Apply Group Policy ACE selected.
At this point, everyone in the Authenticated Users group has this GPO applied including members of the Management Security Group as shown in Figure.
To configure the GPO to apply only to members of the Management group
1. Select the Allow check box for the Apply Group Policy ACE for the Management group.
2. Clear the Allow check box for the Allow Group Policy ACE for the Authenticated Users group.
Note: By changing the ACEs that are applied to different groups, administrators can customize how a GPO affects the users or computers that are subject to that GPO. Write access is required for modifications to be made; Read and Allow Group Policy ACEs are required for a policy to be applied to the group.
To deny GPO application to members of the Management group
Note: Use the Deny ACE with caution. A Deny ACE setting for any group has precedence over any Allow ACE given to a user or computer because of membership in another group.
1. Clear the Allow check box and select the Deny check box for the Apply Group Policy ACE for the Management group.
2. Select the Allow check box for the Allow Group Policy ACE for the Authenticated Users group.
Following Figure shows an example of the security settings that allow everyone to be affected by this GPO, except the members of the Management group, who are explicitly denied permission to the GPO. If a member of the Management group were also a member of a group that had an explicit Allow setting for the Apply Group Policy ACE, the Deny setting would take precedence and the GPO would not affect the user.
3. Click OK and then click Yes to acknowledge the warning about using Deny ACLs.
4. Click OK to close the Headquarters Property page.
21.1 Policy Inheritance
In general, Group Policy is passed down from parent to child containers within a domain. Group Policy is not inherited from parent to child domains. If we assign a specific Group Policy setting to a high-level parent container, that Group Policy setting applies to all containers beneath the parent container, including the user and computer objects in each container. However, if we explicitly specify a Group Policy setting for a child container, the child container’s Group Policy setting overrides the parent container’s setting.
If a parent OU has policy settings that are not configured, the child OU does not inherit them. Policy settings that are disabled are inherited as disabled. In addition, if a policy setting is configured (enabled or disabled) for a parent OU and the same policy setting is not configured for a child OU, the child inherits the parent’s enabled or disabled policy setting.
If a policy setting that is applied to a parent OU and a policy setting that is applied to a child OU are compatible, the child OU inherits the parent policy setting, and the child’s setting is also applied.
If a policy setting that is configured for a parent OU is incompatible with the same policy setting that is configured for a child OU (because the setting is enabled in one case and disabled in the other), the child does not inherit the policy setting from the parent. The policy setting in the child is applied.
21.2 Blocking Inheritance and No Override
The Block Policy inheritance option blocks GPOs that apply higher in the Active Directory hierarchy of sites, domains, and OUs. It does not block GPOs if they have No Override enabled. The Block Policy inheritance option is set only on sites, domains, and OUs, not on individual GPOs. These settings provide complete control over the default inheritance rules.
In the following section, you set up a GPO in the Accounts OU, which applies by default to the users (and computers) in all child objects within the Accounts OU. You then establish another GPO in the Accounts OU and set it as No override. These settings will apply to all child objects even if settings conflict with other settings applied through a GPO. You will then use the Block inheritance feature to prevent group policies set in a parent site, domain, or OU (in this case, the Accounts OU) from being applied to the Production OU.
To create new GPOs
1. In the GPWalkthrough MMC and under securesystem.com, right-click the Accounts OU.
2. Click Properties, and then click the Group Policy tab.
3. Click New, enter Default User Policies for the GPO name, and then press Enter.
4. Click New again, enter Enforced User Policies for the GPO name, and then press Enter.
5. Click the Enforced Users Policies GPO, and then click the Up button to move it to the top of the list.
Note: The Enforced Users Policies GPO should have the highest precedence. Note that this step only serves to demonstrate the functionality of the Up button; an enforced GPO always takes precedence over those that are not enforced.
6. Select the No override setting for the Enforced User Policies GPO by double-clicking the No override column or using the Options button. The Accounts Properties page should now appear as in Figure.
22.1 To enable settings in the Enforced User Policies and Default User Policies GPOs
1. On the Accounts Properties page, double-click the Enforced User Policies GPO.
2. In the Group Policy Object Editor, under User Configuration, expand Administrative Templates.
3. Expand System, and then click Ctrl+Alt+Del Options.
4. In the details pane, double-click the Remove Task Manager policy, click Enabled in the Remove Task Manager dialog box, and then click OK. For more information about the policy, click the Explain tab. The setting is now Enabled as shown in Figure.
5. Click File, and then click Exit to close the Group Policy Object Editor.
6. In the Accounts Properties dialog box, on the Group Policy tab, double-click the Default User Policies GPO in the Group Policy objects links list.
7. In the Group Policy Object Editor, under User Configuration, expand Administrative Templates, expand Desktop, and then click Active Desktop.
8. In the details pane, double-click the Disable Active Desktop policy.
9. Click Enabled, click OK, and then click OK.
10. Click File, and then click Exit to close the Group Policy Object Editor.
Logging on to a client workstation as any user under the Accounts OU, including child OUs, will apply both the Default User and Enforced User GPOs. Both Task Manager and the Active Desktop will be disabled.
23.1 Increasing the Performance of GPOs
Because these GPOs are used solely for user configuration, the computer portion of the GPO can be disabled. Disabling the computer configuration settings reduces the target computer’s startup time as the computer GPOs do not need to be evaluated.
If no computers exist within the Accounts, or any child OUs, disabling the computer portion of the GPO has no immediate benefit. However, since these GPOs could later be linked to a different container that may include computers, you may want to disable the computer side of these GPOs.
To disable the computer portion of a GPO
1. In the Accounts Properties dialog box, right-click the Enforced User Policies GPO, and then select Properties.
2. In the Enforced User Policies Properties dialog box, click the General tab (default), and then select the Disable computer configuration settings check box. In the Confirm Disable dialog box, click Yes, and then click OK to finish.
Note that the General properties page includes two check boxes for disabling a portion of the GPO.
3. Repeat steps 1 and 2 for the Default Users Policies GPO.
23.2 Blocking Inheritance
We can block inheritance so that one GPO does not inherit policy from another GPO in the hierarchy. The following example shows how to block inheritance so that only the settings in the Enforced User Policies affect the users in this OU.
To block inheritance of Group Policy for the Production OU
1. In the Accounts Properties dialog box, click Close.
2. Under the Accounts OU in the GPWalkThrough console, right-click the Production OU, select Properties on the context menu, and then click the Group Policy tab.
3. Select the Block Policy inheritance check box, and then click OK.
To verify that inherited settings are now blocked, you can log on as any user in the Production OU. Note that the Active Desktop is available, however, the Task Manager remains disabled since its disabling GPO was set to No Override in the parent OU.
24.1 Linking a GPO to Multiple Sites, Domains, and OUs
This section demonstrates how you can link a GPO to more than one container (site, domain, or OU) in Active Directory. Depending on the exact OU configuration, you can use other methods to achieve similar Group Policy effects; for example, we can use security group filtering or we can block inheritance. In some cases, however, those methods do not have the desired affects. Whenever you need to explicitly state which sites, domains, or OUs need the same set of policies, use the following method.
To link a GPO to multiple sites, domains, and OUs
1. Under the Accounts OU in the GPWalkThrough console, right-click the Headquarters OU, select Properties on the context menu, and then click the Group Policy tab.
2. In the Headquarters Properties dialog box, on the Group Policy tab, click New to create a new GPO named Linked Policies.
3. Select the Linked Policies GPO, and then click Edit.
4. In the Group Policy Object Editor, under User Configuration and Administrative Templates, click Control Panel, and then click Display.
5. On the details pane, double-click the Prevent changing wallpaper policy, and then click Enabled. Click OK to continue.
6. Click File, and then click Exit to close the Group Policy Object Editor.
7. In the Headquarters Properties page, click Close.
8. Under the Accounts OU in the GPWalkThrough console, right-click the Production OU, click Properties on the context menu, and then click the Group Policy tab on the Production Properties dialog box.
9. Click Add, or right-click the blank area of the Group Policy objects links list, and select Add on the context menu.
10. In the Add a Group Policy Object Link dialog box, click the down arrow on the Look in box, and select the Accounts.contoso.com OU.
11. Double-click the Headquarters.Accounts.contoso.com OU in the Domains, OUs, and linked Group Policy objects list.
12. Click the Linked Policies GPO, and then click OK.
13. Click OK to finish.
We have now linked a single GPO to two OUs. Changes made to the GPO in either location result in a change for both OUs.
25.1 Loopback Processing
Loopback provides alternatives to the default method of obtaining the ordered list of GPOs whose User Configuration settings affect a user. By default, a user’s settings come from a GPO list that depends on the user’s location in Active Directory. The ordered list goes from site-linked to domain-linked to OU–linked GPOs, with inheritance determined by the location of the user in Active Directory and in an order that is specified by the administrator at each level.
Loopback can be set to Not Configured, Enabled, or Disabled, as can any other Group Policy setting. In the Enabled state, loopback can be set to Merge or Replace.
• Loopback with Replace The GPO list for the user is replaced in its entirety by the GPO list that is already obtained for the computer at computer startup. The User Configuration settings from this list are applied to the user.
• Loopback with Merge The GPO list is a concatenation. The default GPOs for computers is appended to the default GPOs for users, and the user gets the User Configuration settings in the concatenated list. Note that the GPO list that is obtained for the computer is applied later and, therefore, it has precedence if it conflicts with settings in the user’s list.
To enable Loopback processing
1. Expand the Resources OU in the GPWalkThrough console, right-click the Desktop OU, click Properties on the context menu, and then click the Group Policy tab in the Desktop Properties dialog box.
2. Click New to create a new GPO named Loopback Policies.
3. Select the Loopback Policies GPO, and then click Edit.
4. In the Group Policy Object Editor, in the Computer Configuration node, expand Administrative Templates, expand System, and then click Group Policy.
5. In the details pane, double-click the User Group Policy loopback processing mode policy.
6. Click Enabled in the User Group Policy loopback processing mode dialog box, select Replace (default) in the Mode drop-down list, and then click OK.
The next section defines restrictive settings for the user’s Start Menu & Taskbar and Desktop environments as might be applied in a Kiosk scenario. To navigate policies efficiently, use the Next Policy navigation buttons in the policy dialog boxes.
To define a restrictive Start Menu & Taskbar environment
1. In the Group Policy Object Editor, in the User Configuration node, expand Administrative Templates, and then click Start Menu & Taskbar.
2. In each of the following policies’ dialog boxes, set the state of the policies as indicated in the table.
Container Policy Setting
Start Menu & Taskbar Remove user’s folders from the Start Menu Enabled
Start Menu & Taskbar Remove links and access to Windows Update Enabled
Start Menu & Taskbar Remove common program groups from Start Menu Enabled
Start Menu & Taskbar Remove My Documents icon from Start Menu Enabled
Start Menu & Taskbar Remove Documents menu from Start Menu Enabled
Start Menu & Taskbar Remove programs on Settings menu Enabled
Start Menu & Taskbar Remove Network Connections from Start Menu Enabled
Start Menu & Taskbar Remove Favorites menu from Start Menu Enabled
Start Menu & Taskbar Remove Search menu from Start Menu Enabled
Start Menu & Taskbar Remove Help menu from Start Menu Enabled
Start Menu & Taskbar Remove Run menu from Start Menu Enabled
Start Menu & Taskbar Remove My Pictures icon from Start Menu Enabled
Start Menu & Taskbar Remove My Music icon from Start Menu Enabled
Start Menu & Taskbar Remove My Network Places icon from Start Menu Enabled
Start Menu & Taskbar Add Logoff to the Start Menu Enabled
Start Menu & Taskbar Remove Logoff on the Start Menu Not Configured
Start Menu & Taskbar Remove and prevent access to the Shut Down command Enabled
Start Menu & Taskbar Remove Drag-and-drop context menus on the Start Menu Enabled
Start Menu & Taskbar Prevent changes to Taskbar and Start Menu Settings Enabled
Start Menu & Taskbar Remove access to the context menus for the taskbar Enabled
Start Menu & Taskbar Do not keep history of recently opened documents Enabled
Start Menu & Taskbar Clear history of recently opened documents on exit Enabled
Start Menu & Taskbar Turn off personalized menus Enabled
Start Menu & Taskbar Turn off user tracking Enabled
Start Menu & Taskbar Add “Run in Separate Memory Space” check box to Run dialog box Not Configured
Start Menu & Taskbar Do not use the search-based method when resolving shell shortcuts Not Configured
Start Menu & Taskbar Do not use the tracking-based method when resolving shell shortcuts Not Configured
Start Menu & Taskbar Gray unavailable Windows Installer programs Start Menu shortcuts Not Configured
Start Menu & Taskbar Prevent grouping of taskbar items Enabled
Start Menu & Taskbar Turn off notification area cleanup Not Configured
Start Menu & Taskbar Lock the Taskbar Enabled
Start Menu & Taskbar Force classic Start Menu Not Configured
Start Menu & Taskbar Remove Balloon Tips on Start Menu items Enabled
Start Menu & Taskbar Remove pinned programs list from the Start Menu Enabled
Start Menu & Taskbar Remove frequent programs list from the Start Menu Not Configured
Start Menu & Taskbar Remove All Programs list from the Start menu Not Configured
Start Menu & Taskbar Remove the “Undock PC” button from the Start Menu Enabled
Start Menu & Taskbar Remove user name from Start Menu Enabled
Start Menu & Taskbar Remove Clock from the system notification area Not Configured
Start Menu & Taskbar Hide the notification area Not Configured
Start Menu & Taskbar Do not display any custom toolbars in the taskbar Enabled
Start Menu & Taskbar Remove Set Program Access and Defaults from Start menu Enabled
To define a restrictive Desktop environment
1. In the Group Policy Object Editor, under the User Configuration and Administrative Templates, click Desktop.
2. In each of the following policies’ dialog boxes, set the state of the policies as indicated in the table.
Container Policy Setting
Desktop Hide and disable all items on the desktop Not Configured
Desktop Remove My Documents icon on the desktop Enabled
Desktop Remove My Computer icon on the desktop Enabled
Desktop Remove Recycle Bin icon from desktop Enabled
Desktop Remove Properties from the My Documents context menu Enabled
Desktop Remove Properties from the My Computer context menu Enabled
Desktop Remove Properties from the Recycle Bin context menu Enabled
Desktop Hide My Network Places icon on desktop Enabled
Desktop Hide Internet Explorer icon on desktop Not Configured
Desktop Do not add shares of recently opened documents to My Network Places Enabled
Desktop Prohibit user from changing My Documents path Enabled
Desktop Prevent adding, dragging, dropping and closing the Taskbar’s toolbars Not Configured
Desktop Prohibit adjusting desktop toolbars Enabled
Desktop Don’t save settings at exit Enabled
Desktop Remove the Desktop Cleanup Wizard Enabled
3. After you have finished setting all the policies, click OK.
4. In the Group Policy Object Editor, navigate to the Active Desktop node under User Configuration\Administrative Templates\Desktops, set the Disable Active Desktop policy to Enabled, and then click OK.
5. In the Group Policy Object Editor, navigate to the Control Panel node under User Configuration\Administrative Templates, and then click the Add/Remove Programs node. Double-click the Disable Add/Remove Programs policy, set it to Enabled, and then click OK.
6. In the Group Policy Object Editor, navigate to the Control Panel node under User Configuration\Administrative Templates, and then click the Display node. Double-click the Remove Display in Control Panel policy, set it to Enabled, and then click OK.
7. In the Group Policy Object Editor, click File, and then click Exit.
8. In the Desktops Properties dialog box, click OK.
All users who log on to computers in the Desktop OU have no policies that would normally be applied to them; instead, they have the user policies defined in the Loopback Policies GPO. You may employ the procedures outlined in the Security Group Filtering section to restrict this behavior to specific groups of computers by creating a security group, and then denying GPO application to that security group.