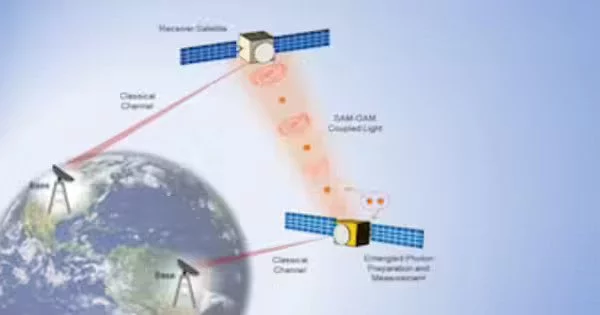
A microlaser chip is a small laser device that has the potential to enhance quantum communication. By incorporating laser technology into quantum communication systems, the microlaser chip can add new dimensions and capabilities, such as increased speed and security. This can lead to more efficient and secure quantum communication networks for a variety of applications.
The qubits used in today’s quantum communication technologies have limited storage space and low interference tolerance because they only have two levels of superposition. The hyperdimensional microlaser developed by Engineering produces ‘qudits,’ photons with four simultaneous levels of information. The increased dimension results in more robust quantum communication technology that is more suitable for real-world applications.
Penn Engineering researchers have developed a chip that outperforms the security and robustness of existing quantum communications hardware. Their technology uses “qudits” to communicate, effectively doubling the quantum information space of any previous on-chip laser.
Liang Feng, Professor in the Departments of Materials Science and Engineering (MSE) and Electrical Systems and Engineering (ESE), along with MSE postdoctoral fellow Zhifeng Zhang and ESE Ph.D. student Haoqi Zhao, debuted the technology in a recent study published in Nature. The group worked in collaboration with scientists from the Polytechnic University of Milan, the Institute for Cross-Disciplinary Physics and Complex Systems, Duke University, and the City University of New York (CUNY).
The biggest challenge was the complexity and non-scalability of the standard setup. We already knew how to generate these four-level systems, but it required a lab and many different optical tools to control all the parameters associated with the increase in dimension. Our goal was to achieve this on a single chip. And that’s exactly what we did.
Liang Feng
Bits, Qubits and Qudits
Non-quantum chips use bits to store, transmit, and compute data, whereas quantum devices use qubits. Bits can be either 1s or 0s, whereas qubits are digital information units that can be both 1 and 0 at the same time. This state of simultaneity is known as “superposition” in quantum mechanics.
To signal these additional dimensions, a quantum bit in a state of superposition greater than two levels is referred to as a qudit.
“In classical communications,” says Feng, “a laser can emit a pulse coded as either 1 or 0. These pulses can easily be cloned by an interceptor looking to steal information and are therefore not very secure. In quantum communications with qubits, the pulse can have any superposition state between 1 and 0. Superposition makes it so a quantum pulse cannot be copied. Unlike algorithmic encryption, which blocks hackers using complex math, quantum cryptography is a physical system that keeps information secure.”
Qubits, on the other hand, aren’t perfect. Qubits have limited storage space and a low tolerance for interference because they only have two levels of superposition. The four-level qudits of the Feng Lab device enable significant advances in quantum cryptography, increasing the maximum secrete key rate for information exchange from one bit per pulse to two bits per pulse. The device has four levels of superposition and allows for further dimension increases.
“The biggest challenge,” says Zhang, “was the complexity and non-scalability of the standard setup. We already knew how to generate these four-level systems, but it required a lab and many different optical tools to control all the parameters associated with the increase in dimension. Our goal was to achieve this on a single chip. And that’s exactly what we did.”
The Physics of Cybersecurity
Photons in tightly controlled states of superposition are used in quantum communication. At the quantum level, properties such as location, momentum, polarization, and spin exist as multiplicities, each of which is governed by probabilities. When a quantum system – an atom, a particle, or a wave – is measured, these probabilities describe the likelihood that it will take on a single attribute.
Quantum systems, in other words, are neither here nor there. They can be found both here and there. Only the act of observation – detecting, looking, and measuring – causes a quantum system to acquire a fixed property. Quantum superpositions, like a subatomic game of Statues, take on a single state as soon as they are observed, making it impossible to intercept or copy them without detection.
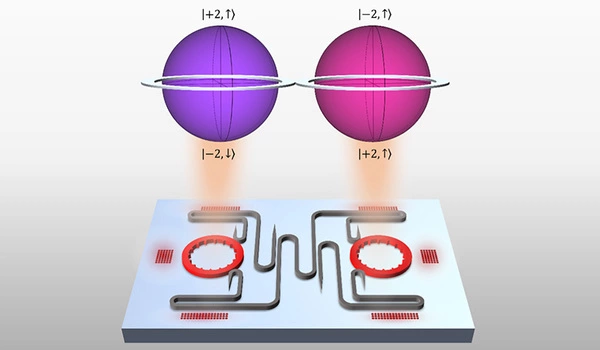
The hyperdimensional spin-orbit microlaser is an extension of the team’s previous work with vortex microlasers, which sensitively tune photon orbital angular momentum (OAM). The most recent device improves on the previous laser’s capabilities by adding another level of control over photonic spin.
This extra level of control – the ability to manipulate and couple OAM and spin – was the breakthrough that enabled them to achieve a four-level system. The difficulty of controlling all of these parameters at once has been a barrier to qudit generation in integrated photonics and represents the team’s major experimental accomplishment.
“Think of the quantum states of our photon as two planets stacked on top of each other,” says Zhao. “Before, we only had information about these planets’ latitude. With that, we could create a maximum of two levels of superposition. We didn’t have enough information to stack them into four. Now, we have longitude as well. This is the information we need to manipulate photons in a coupled way and achieve dimensional increase. We are coordinating each planet’s rotation and spin and holding the two planets in strategic relation to each other.”
Quantum Cryptography with Alice, Bob and Eve
Superposition is used as a tamper-evident seal in quantum cryptography. Randomly generated quantum states are sent back and forth between sender and receiver in Quantum Key Distribution (QKD), a popular cryptography protocol used to test the security of a communications channel.
If the sender and receiver (always Alice and Bob in the cryptography storyworld) discover a certain amount of discrepancy between their messages, they know that their message has been intercepted. However, if the transmission is mostly intact, Alice and Bob believe the channel is secure and use the quantum transmission as a key for encrypted messages.
How does this improve the security of non-quantum communication? We can get a rough idea of how a photon might classically encode the binary digit 1 if we imagine it as a sphere rotating upwards. We can understand 0 if we imagine it rotating downwards.
Eve the eavesdropper can steal, copy, and replace classical photons sent by Alice when they are coded in bits. Even if Eve is unable to decrypt the data she has stolen, she may be saving it for a time when advances in computing technology will allow her to break through.
Quantum communication provides an additional layer of security. Imagine a photon as a sphere rotating upwards and downwards at the same time, simultaneously coding 1 and 0. This is how a qubit maintains dimension in its quantum state.
When Eve attempts to steal, copy, and replace the qubit, her ability to capture the information is jeopardized, and her tampering is visible as a loss of superposition. Alice and Bob will be aware that the channel is insecure and will refuse to use a security key until they can demonstrate that Eve did not intercept it. Only then will they send the encrypted data that was intended using an algorithm enabled by the qubit key.
While quantum physics laws may prevent Eve from copying the intercepted qubit, she may be able to disrupt the quantum channel. Alice and Bob will have to keep generating keys and exchanging them until she stops interfering. Interference patterns are also influenced by accidental disturbances that collapse superposition as the photon travels through space.
The information space of a qubit, which is limited to two levels, has a low tolerance for these errors. Additional dimensions are required for quantum communication to solve these problems. Imagine a photon rotating (as the earth rotates around the sun) and spinning (as the earth spins on its own axis) in opposite directions at the same time. This is how the Feng Lab qudits work.
Eve will be unable to extract any information if she attempts to steal, copy, and replace the qudit, and her tampering will be obvious. The message sent will be much more forgiving of errors, not only from Eve’s interference, but also from flaws introduced as the message travels through space. Alice and Bob will be able to exchange information in an efficient and secure manner.
“There is a lot of concern,” says Feng, “that mathematical encryption, no matter how complex, will become less and less effective because we are advancing so quickly in computing technologies. Because quantum communication relies on physical rather than mathematical barriers, it is immune to future threats. It’s more important than ever to keep developing and refining quantum communication technologies.”