Crafty hackers can create a tool to eavesdrop on some 6G wireless signals in as little as five minutes using office paper, an inkjet printer, a metallic foil transfer, and a laminator. The wireless security hack was discovered by engineering researchers from Rice University and Brown University, who will present their findings and demonstrate the attack this week in San Antonio at ACM WiSec 2022, the Association for Computing Machinery’s annual conference on security and privacy in wireless and mobile networks.
“Awareness of a future threat is the first step in countering that threat,” said study co-author Edward Knightly, Rice’s Sheafor-Lindsay Professor of Electrical and Computer Engineering. “The frequencies that are vulnerable to this attack aren’t in use yet, but they are coming and we need to be prepared.”
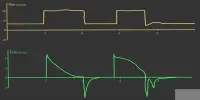
Knightly, Brown University engineering Professor Daniel Mittleman, and colleagues demonstrated in the study that an attacker could easily create a sheet of office paper covered with 2D foil symbols – a metasurface – and use it to redirect part of a 150 gigahertz “pencil beam” transmission between two users.
The attack was dubbed “Metasurface-in-the-Middle” as a nod to both the hacker’s tool and how it is used. Metasurfaces are patterned thin sheets of material that manipulate light or electromagnetic waves. The term “man-in-the-middle” refers to an attack in which an adversary secretly inserts themselves between two parties.
We developed this approach to lower the barrier to fabrication of metasurfaces so that researchers could test many different designs quickly and affordably. Of course, this reduces the barrier for eavesdroppers as well.
Professor Daniel Mittleman
The frequency of 150 gigahertz is higher than that used in today’s 5G cellular or Wi-Fi networks. However, wireless carriers are planning to deploy 150 gigahertz and similar frequencies known as terahertz waves or millimeter waves over the next decade, according to Knightly.
“Next-generation wireless will use high frequencies and pencil beams to support wide-band applications like virtual reality and autonomous vehicles,” said Knightly, who will present the research alongside co-author and graduate student Zhambyl Shaikhanov.
The researchers refer to the two people whose communications are hacked in the study as Alice and Bob. Eve is the eavesdropper’s name. To launch the attack, Eve first creates a metasurface that will diffract a portion of the tight-beam signal to her location. The researchers created a pattern of hundreds of rows of split rings for the demonstration. Each appears to be the letter C, but they are not the same. The open part of each ring varies in size and orientation.
“Those openings and orientations are very specifically done to get the signal to diffract in the exact direction Eve wants,” Shaikhanov explained. “After she designs the metasurface, she prints it on a regular laser printer, and then she uses a hot stamping technique that’s used in crafting. She places a metal foil on the printed paper, feeds it through a laminator and the heat and pressure create a bond between the metal and the toner.”
In a 2021 study, Mittleman and co-author Hichem Guerboukha, a postdoctoral research fellow at Brown, demonstrated that the hot-stamping method could be used to create split-ring metasurfaces with resonances up to 550 GHz.
“We developed this approach to lower the barrier to fabrication of metasurfaces so that researchers could test many different designs quickly and affordably,” Mittleman explained. “Of course, this reduces the barrier for eavesdroppers as well.”
The researchers hope that the study will dispel a widespread misconception in the wireless industry that higher frequencies are inherently secure.
“People have been quoted as saying millimeter-wave frequencies are’covert,’ ‘highly confidential,’ and ‘provide security,'” Shaikhanov said. “‘If you have a super narrow beam, nobody can eavesdrop on the signal because they would have to physically get between the transmitter and the receiver,’ the reasoning goes. We’ve demonstrated that Eve doesn’t have to be overbearing to carry out this attack.”
According to the research, the attack would be difficult for Alice or Bob to detect today. While the metasurface must be placed between Alice and Bob, Knightly believes it “could be hidden in the environment.” “You could cover it up with other sheets of paper, for example.”
Knightly said now that wireless researchers and equipment manufacturers know about the attack, they can further study it, develop detection systems and build those into terahertz networks up front.
“We would have designed it differently if we had known from the beginning, when the internet first came out, that there would be denial-of-service attacks and attempts to take down web servers,” Knightly said. “Building first, waiting for attacks, and then attempting to repair is a much more costly and expensive path than designing securely up front.”
“Millimeter-wave frequencies and metasurfaces are both new technologies that can be used to advance communication, but whenever we get a new communication capability, we must ask ourselves, “What if the adversary has this technology?” What new capabilities will it provide them that they did not have previously? And how can we build a secure network in the face of a formidable adversary?”