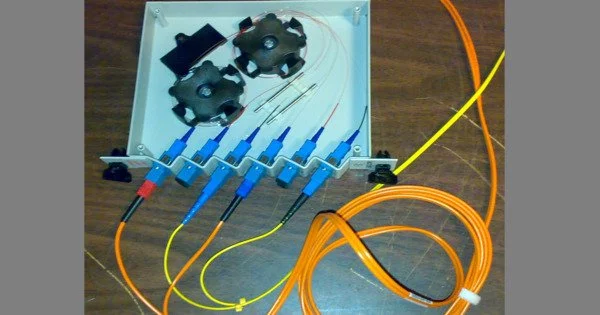
Fiber tapping uses a network tap method that extracts signal from an optical fiber without breaking the connection. Tapping of optical fiber allows diverting some of the signal being transmitted in the core of the fiber into another fiber or a detector. Fiber to the home (FTTH) systems use beam splitters to allow many users to share one backbone fiber connecting to a central office, cutting the cost of each connection to the home. Test equipment can simply put a bend in the fiber and extract sufficient light to identify a fiber or determine if a signal is present.
Fiber tapping is the act of intercepting or listening in on communication transmitted via fiber optic cables. Fiber optic cables use light signals to transmit large amounts of data over long distances. Fiber tapping entails gaining unauthorized access to the information being transmitted via these cables.
Similar techniques can surreptitiously tap fiber for surveillance, although this is rarely done where electronic equipment used in telecommunication is required to allow access to any phone line for tapping by legal authorization. Tapping the fiber means that all signals from every communications source being routed through the fiber are presented and must be sorted for relevant data, an immense task when thousands of sources of data or voice may be present.
Here’s a general overview of how fiber tapping works:
- Physical Access: Physical Access: The first step in fiber tapping is gaining physical access to the fiber optic cable. This can be done by locating the cable infrastructure, which is often buried underground or installed in dedicated ducts or utility poles.
- Cable Interception: After gaining physical access, the attacker must intercept the fiber optic cable. This can be accomplished by either cutting the cable and splicing it with additional components, or by extracting the data without severing the cable using special tools. Fiber optic cables have multiple strands, and the attacker would typically target one or more specific strands to access the data.
- Signal Extraction: The attacker must extract the data signals being transmitted after intercepting the cable. This entails splitting the light signal and redirecting it to a separate location for analysis or interception using specialized equipment. Signals intercepted can be converted back into electronic form for further processing or monitoring.
- Data Analysis: After obtaining the intercepted signals, they can be analyzed to extract the transmitted data. Decoding the light signals back into electronic signals and processing them to retrieve the original information being transmitted, such as voice, video, or data packets, may be required.