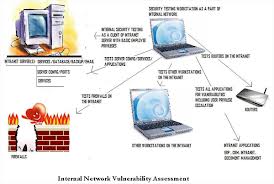
General objective of this article is to focus on Steps for Network Vulnerability Assessments. Network vulnerability assessments work to distinguish and rank vulnerabilities within a system. These assessments are searhing for weaknesses in the system that can allow unauthorized access, flaws or susceptibility of the system, and the likelihood or capacity for exploitation of the flaws.
Steps for Network Vulnerability Assessments