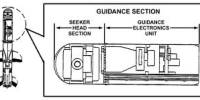
During a social engineering strike, possible predators employ deceptive strategies in order to coerce a new concentrate on businesses staff in to unveiling covered info as well as in to presenting use of methods which contain vulnerable info along with facts. Types of this specific include things like precise phishing email messages, as well as landing pages helpful to collect info. Many e mail attachments exploit recognized vulnerabilities when it comes to putting in unauthorized software around the employee’s laptop or computer. Many popular procedures involved include things like phishing, worms, spyware, detrimental rule, along with Web-based assaults. Other ways of social engineering are usually while essential as an onsite stop by or maybe a call. Based on authorities, some sort of social engineer can warned staff doing all of them imagine these are currently being researched pertaining to wrongdoing.
Social Engineering