While VPN over Tor protects you from your VPN’s view, Tor over VPN gives you more security when accessing the dark web. While each has advantages and disadvantages, you’ll probably use Tor more than VPN.
The premise underlying both strategies is the same, even if they accomplish very distinct goals: you mix Tor and VPN to gain the best of both worlds. Both VPN and Tor have advantages and disadvantages, as we discuss in our comparison piece, and combining them should make both more advantageous.
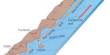
However, this is where theory and reality somewhat diverge. The way these technologies operate prevents direct combination; instead, you must select between two possibilities. Either you connect to your VPN first, then the Tor network, using Tor over VPN, or you connect to your VPN first, then Tor, using VPN over Tor.

Tor Over VPN: Tor over VPN is the way to go if you want the security of a VPN but still need to utilize Tor to access the dark web—though it may help you keep things straight if you think of it as “Tor through a VPN.” By choosing this option, you can still access these websites without having to worry about Tor’s potential security risks.
What implications do those have? Even while Tor is awesome, several lingering questions remain regarding how secure and anonymous it actually is. There is a chance of data leaking even if you use numerous nodes to reroute your connection, let alone if you connect to a hostile node. Additionally, even if your connection is flawless, employing numerous hops will slow down your internet connection, making your visit to Tor’s hidden services a disagreeable experience.
By connecting to a VPN before utilizing Tor, you can get around these problems. It works in a rather straightforward manner: you open your VPN, connect to a local server, and then launch the Tor browser. This will secure your connection to a higher level of encryption, but as Tor is the final link in the chain, dark websites will still accept your connection and let you in.
VPN Over Tor: However, if you use a VPN over Tor or connect to Tor first before using your VPN, dark websites won’t be able to detect your connection. This prevents you from connecting to. onion sites but gives you more anonymity because your location is successfully hidden from your VPN.
When utilizing a dubious free VPN or an ISP that forbids the use of VPNs, such as Russia or China, it can be helpful to utilize VPN over Tor if you don’t trust your VPN provider or if you want to ensure that your ISP can’t tell that you’re using a VPN. Nevertheless, your ISP can still see that you’re using Tor, which could potentially get you into trouble.
Another consideration is the likelihood that this will significantly slow down your connection, particularly if you multi-hop with Tor prior to using the VPN. Additionally, even though your VPN can’t see what websites you’re visiting, unless you signed up anonymously, the service still knows who you are. It would seem foolish to hide your surfing activity from your VPN if you, for example, signed up using a credit card since they already know who you are and may, under some circumstances, reveal your identity to law enforcement.
Deciding Between VPN Over Tor and Tor Over VPN
Both VPN over Tor and Tor over VPN have their applications, but for the majority of users, Tor over VPN will be the superior option. It allows you to connect to Tor’s hidden services while resolving some of Tor’s security vulnerabilities. In fact, several VPNs include it as a built-in function because it is so helpful. There are others, but NordVPN and ProtonVPN are the two greatest examples.
However, a VPN via Tor is rather less beneficial. Its primary purpose is to hide you from your VPN’s gaze, which begs the question of why you’re using one in the first place. If your privacy is a top priority, you would be much better off using a privacy-conscious VPN like Mullvad or IVPN than tinkering with Tor configurations.