Security measures of Banking Activates, a case study
on The City Bank Limited
As a financial institution, Banks are highly secure in general. In our daily banking activities administration people are committed to provide every kind of security matter from employee to customer satisfaction. There are so many security compliances from Bangladesh Bank under the act of financial institution and general banking. In each and every activities of commercial Banks Bangladesh Bank has impose various guide line and checked those compliance in a systematic way by the audit committee monitoring.
As this conscience CBL General Admin Division provided all the support to the concern department and all the CBL branches not only in Bangladesh also all over the world. CBL is fully automated and centralized bank, as a result head office needs to work 24 hours in a day and 30 days in a month. For monitoring all the security issues and providing support here in CBL a special control room fully operational 24hours in a day with 4 security supervisors and 12 securities personal. Behind the scene there are lot of automated software also in operation for smooth and fast support.
From the control room CBL administration can monitored each and every branch from Syedpur, Nilfapmarti to Cox Bazar, Chittagong along with 5 different back offices include the CBL city center and also 300+ ATM booths. All this accumulated by CBL IT which is major concern of security of CBL, and the second priority is ADC (Alternative Delivery Channel), ADC is specialized in various banking activities for the entire baking support that’s why we call it banking backbone, so generally it’s very important security issue for GAD. And the third priority is the CARD Division.
Objective
As an officer of CBL and doing internship it’s really great experience, I chose this topic because here I engaged with this type of work and what I am seeing here is actually outstating. Therefor my reset is growing up to prepare a project on it. And also informing to others that when a person enters in the premises and leave from that premises how he or she been monitored every moment.
Methodology
Methodology is the systematic, theoretical analysis of the methods applied to a field of any study. It comprises the theoretical analysis of the body of methods and principles associated with a branch of knowledge. Typically, it encompasses concepts such as paradigm, theoretical model, phases and quantitative or qualitative techniques. Here methodology is applied full systematically.
Primary Data Collection:
- Interviews with departmental head.
- Departmental surveys.
- Observation.
- On the job trainings.
- Practical working experiences.
Secondary Data Collection:
- Bangladesh Bank’s Security Guidelines.
- Annual Report of the City Bank Limited.
- Government General Security policies.
- World Bank’s Security publication.
- News articles of Security issues.
Introduction
City Bank is one of the most established private Commercial Banks working in Bangladesh. It is a top bank among the oldest five Commercial Banks in the country which began their operations in 1983. CBL started their journey on 27th March 1983 through opening its first branch at B. B.
Avenue Branch in the capital, Dhaka city. It was the visionary enterprise of around 13 local businessmen who overcame the immense instabilities and risks with courage and enthusiasm that made the foundation & forward walk of the bank conceivable. Those patron chiefs started the excursion with just Taka 3.4 crore worth of Capital, which now is a respectable Taka 2311.78 crore as capital & reserve. City Bank is among the very few local banks which do not follow the traditional, decentralized, geographically managed, branch based business or profit model.
Instead the bank manages its business and operation vertically from the head office through 5 distinct Units namely
- Business Unit
- Branch Banking
- Risk Unit
- Operations Unit
- Support
Under a real-time online banking platform, these 5 distinct Units are supported at the back by a robust service delivery or operations setup and also a smart IT Backbone. Such centralized business segment based business & operating model ensure specialized treatment and services to the bank’s different customer segments.
The bank currently has total 112 branches which includes 99 online branches, 1 full-fledged Islamic Banking branch, 1 SME service center and 11 SME/Agri branches spread across the length & breadth of the country. Besides these traditional delivery points, the bank is also very active in the alternative delivery area. It currently has 253 ATMs of its own; and ATM sharing arrangement with partner banks that has more than 1150 ATMs in place; SMS Banking; Interest Banking and so on. It already started its Customer Call Center operation.
SECURITY MEASURES OF BANKING ACTIVITIES
IT Security and Policies
CBL administration division all the time engaged to IT division for full security support. CBL is fully automated bank therefore admin almost 60% resource use to cover every IT security policy given by the Bangladesh Bank, Here the some policies regarding to IT security and policies are given as it is from Bangladesh bank guidelines.
The banking industry has changed the way they provide services to their customers and process information in recent years. Information and Communication Technology (ICT) has brought about this momentous transformation. Security of Information for a financial institution has therefore gained much importance, and it is vital for us to ensure that the risks are properly identified and managed. Moreover, information and information technology systems are essential assets for the banks as well as for their customers and stake‐ holders. Information assets are critical to the services provided by the banks to their customers. Protection and maintenance of these assets are critical to the organizations’ sustainability. Banks must take the responsibility of protecting the information from unauthorized access, modification, disclosure and destruction. Bangladesh Bank has impose a Guideline for ICT Security for banks & FIs to be used as a minimum requirement and as appropriate to the level of computerization of their operations.
Categorization of banks/branches/units depending on ICT Operation
The locations for which the ICT Security Guideline is applicable i.e., the Head Office, Zonal Office, Branch and/or Booth/Unit of a bank or FI may be categorized into three tiers depending on their ICT setup and operational environment/procedures as:
Tier‐1: Centralized ICT Operation through Data Center (DC) including Disaster Recovery Site (DRS) to which all other offices, branches and booths are connected through WAN with 24×7 hours attended operation.
Tier‐2: Head Office, Zonal Office, Branch or booth having Server to which all or a part of the computers of that locations are connected through LAN.
Tier‐3: Head Office, Zonal Office, Branch or booth having standalone computer(s).
ICT Security Policy
Every bank having Information systems must have an ‘ICT Security Policy’ which must be fully complied with this ICT Security Guideline and be approved by the board of the bank. For foreign banks, the documents must also be in conformity with their global policy documents.
Physical Security for Tier‐1
Data Center Access
- Physical security shall be applied to the information processing area or Data Center.
- Data Center must be a restricted area and unauthorized access shall be prohibited.
- Entrance into the Data Center shall be restricted.
- Access authorization procedures shall exist and be applied to all persons (e.g. employees and vendors). Unauthorized individuals and cleaning crews must be escorted during their stay in the Data Center.
- Access authorization list shall be maintained and reviewed periodically for the authorized person to access the Data Center.
- Access log with date, time and purpose shall be maintained for the vendors, service providers and visitors entered into the Data Center.
- Security guard shall be available for 24 hours.
- Emergency exit door shall be available.
Physical Security for Tier‐2
Server Room Access
- Server room must have a glass enclosure with lock and key with a responsible person of the Branch.
- Physical access shall be restricted, visitors log must exist and to be maintained for server room.
- Access authorization list must be maintained and reviewed on regular basis.
Physical Security for Tier‐3
Computer Room Access
- The PC running the branch banking software must be placed in a secured area and held by a responsible person in the Branch.
- Access authorization list must be maintained and reviewed on a regular basis.
Credit Card Operations
Credit Card:
The term “Credit Card” generally means a plastic card issued by Scheduled Commercial Banks (SCBs) assigned to a Cardholder, with a credit limit, that can be used to purchase goods and services on credit or obtain cash advances.
For issuing Credit Card prior approval of BB is not necessary. With the approval of their Board of Directors banks can issue credit cards.
Billing Process:
These processes are specified by the Bangladesh Bank, Bank providing the payment card services must comply with the industry security standards, e.g.‐ Payment Card Industry Data Security Standard (PCI DSS) to ensure the security of cardholder’s data. The PCI DSS includes following requirements for security management, policies, procedures, network architecture, software design and other protective measures:
- PINs used in transactions shall be processed using equipment and methodologies to ensure that they are kept secured.
- Cryptographic keys used for PIN encryption/decryption and related key management shall be created using processes to ensure that it is not possible to predict any key or determine that certain keys are more probable than other keys.
- Secret or private Keys shall be conveyed or transmitted in a secured manner.
- Unencrypted Key loading to hosts and PIN entry devices shall be handled in a secured manner.
- Randomized Keys shall be used in a manner that prevents or detects their unauthorized usage.
- Keys shall be administered in a secured manner.
- Equipment used to process PINs and keys shall be managed in a secured manner.
Card Printing and Packaging
- Delivering to Client by the specific authorized service provider.
- Special ploy packaging, which is very first in the Bangladesh.
- Central data base all the delivering information.
Cash Transit Process
Cash Transit process is carrying the Treasury note to various locations, but there are some specific process should be maintained.
- Principal Branch/Main Branch/Head office they are the only hub for the cash transits.
- Vehicle only can mobilize for this place
- Special vehicle and special armed security on board
- One security office and One cash teller
Treasury (Cash/Gold) Vault Security
Vault security cannot be disclose, Bangladesh Bank restricted to publish any security policies regarding cash vault or treasury vault.
But here are some policies regarding security of vault
- RCC pillars with 12’inch thin concrete wall.
- Vibration detector must be installed
- Infrared and thermal camera
- Access control with special finger detection system.
Secure document dispatching
CBL is centralized bank, all the functions of banking still controlling from head office and smooth operation there are 73 individual department worked all together.
CBL dispatch service is totally different bank in Bangladesh, after the Standard Chartered Bank
CBL has the own dispatch automation system in Bangladesh, which is called Dispatch Management System.
CBL dispatch has 2 wing located at motijheel, those are given below,
- Internal (CBL to CBL – All Branches/Head office/Back office)
- External (Client/Service provider)
Fraud Detection
For any kind of fraud detection CBL admin have to provide various evidence to Internal Control and Compliance Division. Other hand there are so many compliance also guided by Bangladesh Bank too.
CCTV surveillance
- Every floor (standard Size) must be fully cover-up in CCTV surveillance
- CCTV footage must be stored minimum 6 months
- Infrared, Motion detection system must be installed too.
- Special team or service provider must be assign for any support
ATM Booth surveillance
CBL Admin and ADC combine operate a team called IM (Infrastructure Maintenance Team), they are surveillance and reporting 24 hours to their in charge, this team works as roster basis.
Bank Note, Cheque tester
In general admin there is a special unit call logistic, they are assign to provide all kind of machine regarding Bank Note and Cheque testing. Usually this machine are called UV Machine
Access Control
In the CBL access control is one of the important part of the security, and there also Bangladesh Bank guide line and other government security issues related to access control.
TMS (Access Security Software)
In computer security, general access control includes authorization, authentication, access approval, and audit. A more narrow definition of access control would cover only access approval, whereby the system makes a decision to grant or reject an access request from an already authenticated subject, based on what the subject is authorized to access. Authentication and access control are often combined into a single operation, so that access is approved based on successful authentication, or based on an anonymous access token. Authentication methods and tokens include passwords, biometric scans, physical keys, electronic keys and devices, hidden paths, social barriers, and monitoring by humans and automated systems
- Access control systems provide the essential services of CBL authorization, identification and authentication (I&A), access approval, and accountability where
- Authorization specifies what a subject can do, It’s a combine security key form admin and IT
- Identification and authentication ensure that only legitimate subjects can log on to a system
- Access approval grants access during operations, by association of users with the resources that they are allowed to access, based on the CBL admin authorization policy
- In general Human Resource accountability for create identifies of employees and their information (or all subjects associated with a user).
Branch Operation procedures
- Branch operation manager’s activities, General Guide line by the CBL Branch operation division.
- Daily operation procedures, General Guide line by the CBL Operation division.
Guarding
- Posting Guards
- Gun policy
- Gun man policy
Fire and Safety
Fire and safety issue is compliance with Fire service department, Although GAD is responsible for that, Fire and Safety issuers are
- Alarm System
- Exit process
- Automated fire extinguisher
- Manual or Mobile fire extinguisher
- Water connections
Evacuation Drill
As per Bangladesh Bank guides evacuation drill must be practice in below mentioned manner,
- For each location (Head office/ Back office/ Branch) yearly minimum 2times drill should be done.
- Depend on size adequate space for evacuation zone.
- Form every department 2 person should be selected for volunteer.
Observational analysis
As an officer of CBL and being part of security team it is very hard to work here to comply full guidance of Bangladesh Bank and other Government organization, But for all outsider they cannot understand what the play is going on behind the seen. In my 2 year career, have learn too many thing about security issue, but yes although I’m student of business area these are not my filed. But still I believe working in a structured way is very mush effective to learning and build up career too.
CBL admin division really work heard very day to smoothen the work, huge work load but its distributed to each and every person of CBL GAD, so that operation not hampered. Admin support all the other department flawlessly and every time ready to face any kind of incident at anywhere in Bangladesh to protect property of CBL.
ANALYSIS AND COMPLIANCE
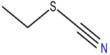
Strategic Group Mapping Analysis
Strategic group mapping is a tool to understand actual position of any organization in the same industry for a specific matter. This report about all of the security measures, therefore it’s very rational to understand where the CBL is standing about the security measure compare to all of the banks operate in Bangladesh.
Tools of strategic group mapping,
In this report, here two major aspects considered as a basic tools for group mapping
- Investment in security: The total capital that invested in security system to ensure all the security measures.
- Service Quality: Ensuring the level of security quality to the client and other services.
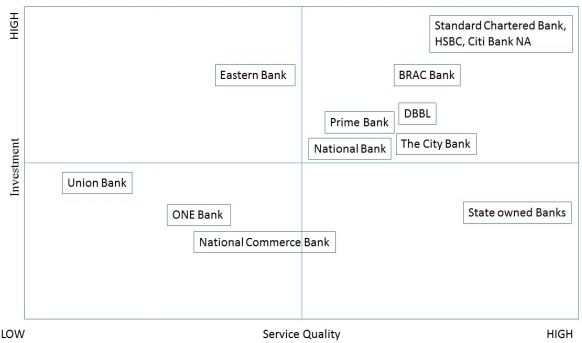
Figure: Strategic Group Mapping of Bangladeshis Banking
Benchmark Analysis
Benchmark analysis will tell us what should be the standards required for security measures by the Bangladesh Bank with all other related government organizations and where the CBL meet that benchmark or not.
Intruder Alarm System
Intruder alarm system that detected any unwanted entry in the organization’s premises, especially during off times. Although in our county this type of security system is very rare. Recently, Bangladesh bank introduced to the Banks and other financial institution to install this system as a pilot basis.
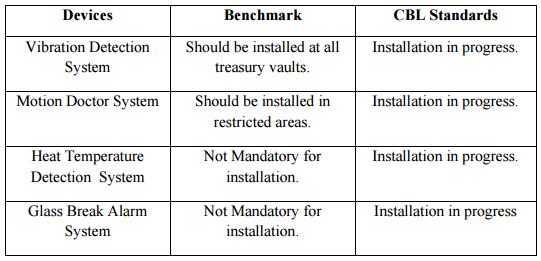
Table: Intruder Alarm System – Benchmark
Environment Protection System
Environment protection system is like general security for the all employees, as like entry and exit process in a Branch or Head office, General guide line for security, restriction etc. Now by the systematic survey here I draw sorting to understand the environment protection system.
Infrastructure and Architectural System
This segment is not regulated by Bangladesh Bank, it’s all about civil defiance authority, Local Government authority (for rural areas), Rajuk (Rajdhani Unoyon Kortipokkha) and City Corporation. Bangladesh Bank’s monitored this segment by the circular of BRPD (Banking Regulation and Policy Department).
Fire Alarm and Evacuation System
Now days this is one of the most important issue. Government is very restricted about this issue along with Bangladesh Bank too. For a financial institution they have several regulatory board to monitor this fire and evacuation system. After the recent Nepal earthquake, Bangladesh Bank issued an emergency circular to the Banks to investigate the entire infrastructure thoroughly as guides by civil defiance authority.
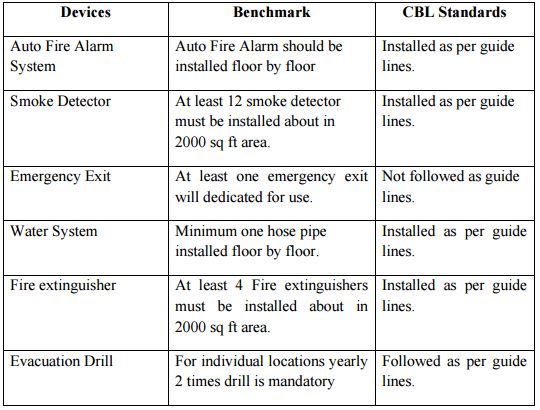
Table: FA System – Benchmark
Cash Transit Security System
For Banks and Financial system cash transit security is very important, Bangladesh Bank and government regulated this issue very strictly. By the various secondary data collection and observation here given some comparison analysis between regulation of guide line and CBL standard.
Document Security while Dispatching
Dispatching documents or any other security item is very important, As per Bangladesh Bank compliance and other security policy all together ensure a secure dispatching. CBL have achieved tremendous benchmarking among the all banks operate in Bangladesh. Here the observation of the benchmark and CBL standard comparison.
Central Storing System
The City Bank Limited is the only bank have special department call DSS that fully compliance for central storage system with a 6000 sq ft three stored. All other bank follows this compliance but not like the CBL with a dedicated building and for bank keep the all documents is compulsory.
Connectivity Security System
Connectivity security is very important for banks, basically it’s required for ATM machine and Finacle online transitions. Recently POS terminals are also need connectivity security. POS (Point of Sale) is actually a machine for use plastic cards, it use mobile SIM cards for connectivity. All those connectivity need to be secure. ADC deal with all this connectivity and admin is for further monitoring and maintainer. Benchmark for connectivity security system,
SWOT ANALAYSIS
Strength
- CBL have the long baking experience in order to compete security issue.
- Amex standard service.
- Advance technology and IT infrastructure.
- For any security matter CBL have own administration division.
- Most of the Army persons are dealing with all type of security issues.
- Good understating between each department.
- Advance Centralization Banking system.
- Fully automated banking.
- Advance internet banking.
- Secure internet banking protocol.
- Advance ATM machine, Walk though ATM system first in Bangladesh.
- Most secure AMEX protocol.
Weakness
- Too much corporate complexity to impose any new policy.
- Technology is change every day but for Bank it’s very hard apply any technological change overnight.
- Under the cost cutting rules, some major security part has been declined.
- Bank’s own security guards are lazy compare to other service provider guards.
- IT infrastructure need to be relocated, because for recent earthquake it’s became little unstable.
- There are different build occupied as CBL back office in very scattered location of Dhaka City, As a result communication kills so many productive time.
- As a financial institution, less attention to upgrade or maintained security issue compare to Bank’s business unit.
- Employee benefits is little lower in Head office compare to working in Branch.
- Increasing of work load every day but resource is limited.
- Fire and Safety system is out dated.
- Business unit getting the highest priority among the all unit.
- Grade of Guards are not satisfactory.
- Fire arms getting back dated.
- CCTV and footage storage not that much adequate.
- On demand no reserve security personal or guards.
Opportunity
- Increasing service quality that also helps to increase client.
- Provide most secure online portal and payment system.
- Capacity to control more branches that means no extra problem in technical side.
- Huge IT infrastructure, for proving smooth operation.
- With Centralize Banking System, Banking is more secure compare to all other decentralize banking system.
- City Touch, first time in Bangladesh with whole Banking facility.
- Huge Admiration support, for securing every matter related to security.
- Special security unit, Helps to improve service quality.
- Advance security equipment’s, fully compliance to others.
Threat
- Everyday new type of security issue arises.
- New kind of general thief t attempts.
- New kind of technological fraud attempts.
- Vulnerable condition of law and order
- Unstable government security support.
- Using lower grade guard.
- Regular upgrading problem.
- Very competitive client service and satisfaction.
- Bangladesh Bank compliance and audit issue.
- New Banks with more security.
- Need more effective trainings.
Compliance
By this compliance chart we can understand CBL achieving compliance comparing locally and the international standard of same industry,
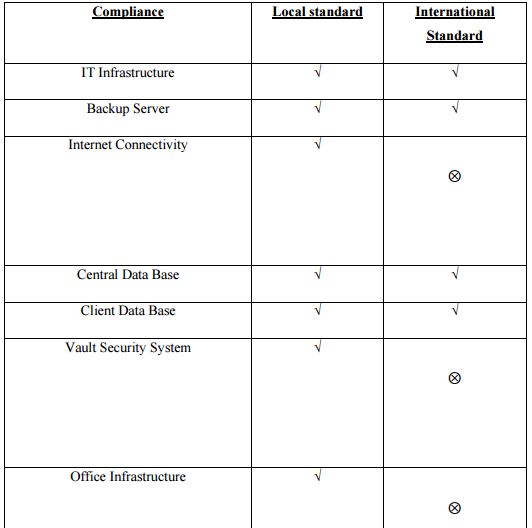
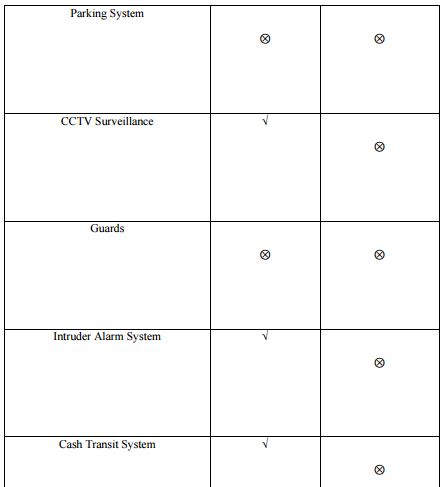
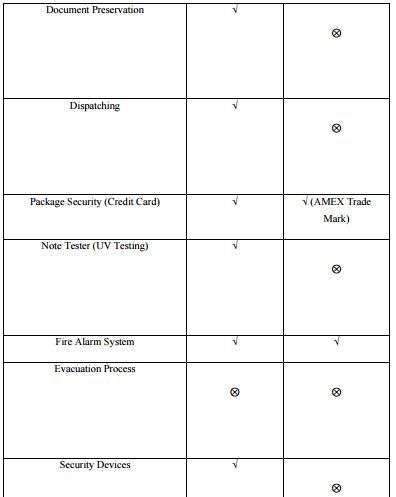
Security Factors Comparing to Other Banks
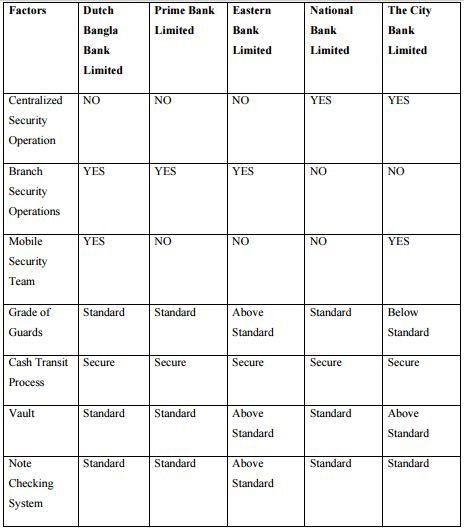
Client Satisfaction
According to several new and articles of customers satisfaction in security system regarding local banks,
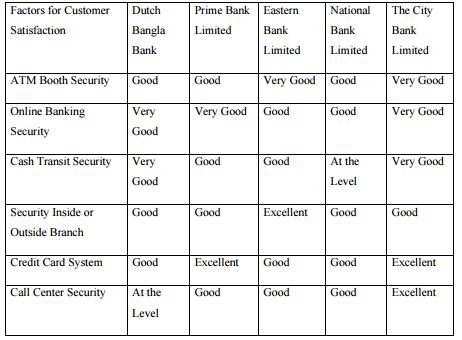
FINDINGS
In the finding part I tried to accumulated all the matters through I described in this report,
- CBL general admin division and the security team are dedicated to all security issues. As we know in banking sector admin is generally called common service division. But in CBL admin has huge work area form designs a branch / office / ATM etc to secure all the assets.
- CBL admin have organized advance security operations, Which is fully compliance to Bangladesh Bank circular and other circular of government organizations
- CBL IT has advance secure protocol system, which has most secure internet protocols and Banking connectivity. Bangladesh Bank ICT policy is fully obliged and ISO9001 certified too.
- AMEX Standard Bank, after the collaboration to the AMEX its mandatory to have the minimum level of standard of Banking. Here City Bank obtained huge popularity and service to the client.
- Employee rank and designation problem, In the CBL some point employee are not getting the full appreciation and benefits.
- Challenging job, in the admin there are no job like target achieving or product lunching, rather here people are engaged with several challenging task, its start form MacMom with a situation, Divisional head direction and ends with leading by Department heads. Every day new task and new kind of solution.
- Understanding behind the scene of security measures, yes it’s a great opportunity to work with CBL in admin division, as a business student we need to know this kind of matters beside the business arena and that can be very good to build up career.
Recommendation
- Management should pay little attention to security system, because now a days security is big concern
- For apply any advance technology Bangladesh Bank and Bangladesh Government should have individual cell tor technological advancement.
- Need more facilities to the existing guards, that can be improve their motivation which is very important.
- IT division should more cooperative with Admin, because major security concern for Admin is IT.
- HRD needs to emphasize on Head office employees too.
- Organized work distribution need on urgent basis, because it’s happed productivity.
- Immediately Fire and Safety system need to be update.
- CCTV and Footage storage capacity need to be update, Hence CBL maintained the Bangladesh Bank guidance of this policies.
Conclusion
As we know The City Bank, established in 1983, is 1st generation personal industrial banks during this country and is that the best bank in terms of adopting international best practices by doing away with old ancient redistributed banking model and culture. The main focus of the “transformation” project was conjointly on up the general quality of assets; re-launching the complete anew; investment the technology potential; up the standard of product offerings and inserting abundant higher benchmarks for client service.
CBL complete is already recognized because the “most purported reworking establishment within the country” and currently it’s poised to become the “Most purported establishment Brand” before long. The Bank goes to launch Priority Banking services for top internet price people in 2013. This year can see the launches of Mobile Banking for unbanked individuals, Pt securities market card for the highest finish of the market, the country’s 1st Business-to-Business (B2B) card and then on.
So this report is not apart from the business aspects of the back which has been just talked right above, it’s about security which is supportive for operate the banking system every day 24 hours and 365 days in a year. Here I trying to just informing some security aspects of banking activities and what the actual seen happened every.