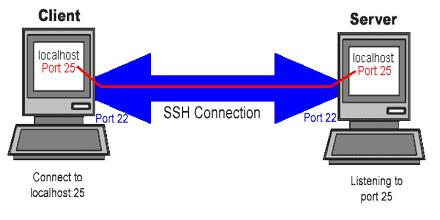
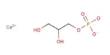
Secure Shell is widely used by network administrators for managing systems and applications remotely, allowing them to log in to another computer over a network, execute commands and move files from one computer to another. It provides strong authentication and secure encrypted data communications between two computers connecting over an insecure network such as the Internet. It uses public-key cryptography to authenticate the remote computer and allow it to authenticate the user, if necessary. There are several ways to use Secure Shell; one is to use automatically generated public-private key pairs to simply encrypt a network connection, and then use password authentication to log on.
Secure Shell