WiMAX :
WiMAX is called the next generation broadband wireless technology which offers high speed, secure, sophisticate and last mile broadband services along with a cellular back haul and Wi-Fi hotspots. The evolution of WiMAX began a few years ago when scientists and engineers felt the need of having a wireless Internet access and other broadband services which works well everywhere especially the rural areas or in those areas where it is hard to establish wired infrastructure and economically not feasible. IEEE 802.16, also known as IEEE Wireless-MAN, explored both licensed and unlicensed band of 2-66 GHz which is standard of fixed wireless broadband and included mobile broadband application.. The IEEE 802.16e air interface based on Orthogonal Frequency Division Multiple Access (OFDMA) which main aim is to give better performance in non-line-of-sight environments . IEEE 802.16e introduced scalable channel bandwidth up to 20 MHz, Multiple Input Multiple Output (MIMO) and AMC enabled 802.16e technology to support peak Downlink (DL) data rates up to 63 Mbps in a 20 MHz channel through Scalable OFDMA (S-OFDMA) system. IEEE 802 .16e has strong security architecture as it uses Extensible Authentication Protocol (EAP) for mutual authentication, a series of strong encryption algorithms, CMAC or HMAC based message protection and reduced key lifetime.
WiMAX at a Glance:
The IEEE standard committee introduced standards for networking elements, for an instance, IEEE 802.16 in 1999. The 802.16 family standard is called Wireless Metropolitan Area Network (MAN) commercially known as WiMAX (Worldwide interoperability for Microwave Access) which is an industry-led, non profit organization and responsible for testing, certificating and promoting the compatible interoperable wireless products based on IEEE 802.16 working group and ETSI’s HiperMAN standard . The original IEEE standard addressed 10 to 66 GHz in licensed bands and 2 to 11 GHz in unlicensed frequency range. Time to time, they certified different versions of WiMAX based on different criteria such as carrier based wireless, fixed and portable wireless devices etc .
Introduction
WIMAX is a technology based on the IEEE 802.16 specifications to enable the delivery of last-mile wireless broadband access as an alternative to cable and DSL. The design of WI-MAX network is based on the following major principles:
Features of WiMAX
There are certain features of WiMAX those are making it popular day by day. Some important features of WiMAX are described below:
Interoperability
This is the main concern of WiMAX. The IEEE 802.16 standard is internationally accepted and the standard is maintained and certified by WiMAX forum which covers fixed, portable and mobile deployments and giving the user the freedom to choose their product from different certified vendors and use it in different fixed, portable or mobile networks .
Mobility
WI-MAX offers immense mobility especially IEEE 802.16e-2005 as it adopted SOFDMA (Scalable Orthogonal Frequency Division Multiple Access) as a modulation technique and MIMO (Multiple Input Multiple Output) in its physical layer. There are two challenges in wireless connectivity, one of them is for session initiation, which provides a mean to reach to inactive users and continue the connection service by extending it even the home location of that user has been changed and the other one provides an ongoing session without interruption while on moving (specially at vehicular speed. The first is known as roaming and the second one is handoff. These two are described below
(a) Roaming
The centralized database keeps current information which sends to the network by the user base station when it moves from one location to another. To reach another subscriber station the network pages for it using another base station. The used subscriber station for paging depends on updating rate and movement of subscriber station – that means from one station to another . To perform this operation, there are several networking entities involved such as NSS (Network Switching Subsystem), HLR (Home Location Register) and VLR (Visitor Location Register) etc.
(b) Handoff
Due to the absence of handoff technique, the Wi-Fi users may move around a building or a hotspot and be connected but if the users leave their location, they lose their connectivity. But with the 802.16e-2005, the mobile users will be connected through Wi-Fi when they are within a hotspot and then will be connected to 802.16 if they leave the hotspot but will stay in the WiMAX coverage area .
Accessibility
To get high speed network connectivity, only necessary thing is to become a subscriber of WiMAX service providers. Then they will provide hardware that is very easy to install. Most of time hardware connects through USB ports or Ethernet and the connection may be made by clicking button.
Robust Security
WiMAX have a robust privacy and key management protocol as it uses Advanced Encryption Standard (AES) which provides robust encryption policy. It also supports flexible authentication architecture which is based on Extensible Authentication Protocol (EAP) which allows variety of subscriber credentials including subscriber’s username and password, digital certificates and cards.
WI-MAX Architecture
WiMAX architecture comprises of several components but the basic two components are BS and SS. Other components are MS, ASN, CSN and CSN-GW etc. The WiMAX Forum’s Network Working Group (NWG) has developed a network reference model according to the IEEE 802.16e-2005 air interface to make sure the objectives of WiMAX are achieved. To support fixed, nomadic and mobile WiMAX network, the network reference model can be logically divided into three parts.
Mobile Station (MS)
It is for the end user to access the mobile network. It is a portable station able to move to wide areas and perform data and voice communication. It has all the necessary user equipments such as an antenna, amplifier, transmitter, receiver and software needed to perform the wireless communication. GSM, FDMA, TDMA, CDMA and W-CDMA devices etc are the examples of Mobile station.
The Benefits of MIMOs
OFDM has some key advantages over other widely-used wireless access techniques, such as Time Division Multiple Access (TDMA), Frequency Division Multiple Access (FDMA) and Code Division Multiple Access (CDMA). The main merit of OFDM is the fact that the radio channel is divided into many narrow-band, low-rate, frequency-nonselective subchannels or subcarriers, so that multiple symbols can be transmitted in parallel, while maintaining a high spectral efficiency. Each subcarrier may deliver information for a different user, resulting in a simple multiple access scheme known as Orthogonal Frequency Division Multiple Access (OFDMA). This enables different media such as video, graphics, speech, text, or other data to be transmitted within the same radio link, depending on the specific types of services and their Quality-of-Service (QoS) requirements.
High data-rate wireless communications have attracted significant interest and constitute a substantial research challenge in the context of the emergingWLANs and other indoor multimedia networks. Specifically, the employment of multiple antennas at both the transmitter and the receiver, which is widely referred to as the Multiple-Input Multiple- Output (MIMO) technique, constitutes a cost-effective approach to high-throughput wireless communications.
Mobile terminals antennas
The possibility of “auto search” and continuous beam tracking are extremely important for other class of the equipment – mobile user’s terminals. In such a case, making use of an omni directional antenna, gives very poor quality of signal and as a result, communication throughput is very low. In this case additional external multibeam antenna with 10 dBi gain.
HANDOVER INTRODUCTION
The term handover or handoff refers to the process of transferring an ongoing call or data session from one channel connected to the core network to another. The most basic form of handover is when a phone call in progress is redirected from its current cell (called source) and its used channel in that cell to a new cell (called target) and a new channel.
In telecommunications there may be different reasons why a handover might be conducted:
when the phone is moving away from the area covered by one cell and entering the area covered by another cell the call is transferred to the second cell in order to avoid call termination when the phone gets outside the range of the first cell;
when the capacity for connecting new calls of a given cell is used up and an existing or new call from a phone, which is located in an area overlapped by another cell, is transferred to that cell in order to free-up some capacity in the first cell for other users, who can only be connected to that cell;
in non-CDMA networks when the channel used by the phone becomes interfered by another phone using the same channel in a different cell, the call is transferred to a different channel in the same cell or to a different channel in another cell in order to avoid the interference;
again in non-CDMA networks when the user behaviors changes, e.g. when a fast-traveling user, connected to a large, umbrella-type of cell, stops then the call may be transferred to a smaller macro cell or even to a micro cell in order to free capacity on the umbrella cell for other fast-traveling users and to reduce the potential interference to other cells or users (this works in reverse too, when a user is detected to be moving faster than a certain threshold, the call can be transferred to a larger umbrella-type of cell in order to minimize the frequency of the handovers due to this movement) .
in CDMA networks a (see further down) may be induced in order to reduce the interference to a smaller neighboring cell due to the “near-far” effect even when the phone still has an excellent connection to its current cell;
Types of handover
A hard handover is one in which the channel in the source cell is released and only then the channel in the target cell is engaged. Thus the connection to the source is broken before or ‘as’ the connection to the target is made—for this reason such handovers are also known as break-before-make. Hard handovers are intended to be instantaneous in order to minimize the disruption to the call. A hard handover is perceived by network engineers as an event during the call [15]. It requires the least processing by the network providing service. When the mobile is between base stations, then the mobile can switch with any of the base stations, so the base stations bounce the link with the mobile back and forth. This is called ping-ponging
Fig : Hard handover
Soft handover is one in which the channel in the source cell is retained and used for a while in parallel with the channel in the target cell. In this case the connection to the target is established before the connection to the source is broken, hence this handover is called make-before-break [15]. The interval, during which the two connections are used in parallel, may be brief or substantial. For this reason the soft handover is perceived by network engineers as a state of the call, rather than a brief event. Soft handovers may involve using connections to more than two cells: connections to three, four or more cells can be maintained by one phone at the same time [15-16]. When a call is in a state of soft handover, the signal of the best of all used channels can be used for the call at a given moment or all the signals can be combined to produce a clearer copy of the signal. The latter is more advantageous, and when such combining is performed both in the downlink (forward link) and the uplink (reverse link) the handover is termed as softer. Softer handovers are possible when the cells involved in the handovers have a single cell site.
Comparison of handovers
An advantage of the hard handover is that at any moment in time one call uses only one channel. The hard handover event is indeed very short and usually is not perceptible by the user. In the old analog systems it could be heard as a click or a very short beep, in digital systems it is unnoticeable. Another advantage of the hard handoff is that the phone’s hardware does not need to be capable of receiving two or more channels in parallel, which makes it cheaper and simpler. A disadvantage is that if a handover fails the call may be temporarily disrupted or even terminated abnormally. Technologies, which use hard handovers, usually have procedures which can re-establish the connection to the source cell if the connection to the target cell cannot be made. However re-establishing this connection may not always be possible (in which case the call will be terminated) and even when possible the procedure may cause a temporary interruption to the call.
One advantage of the soft handovers is that the connection to the source cell is broken only when a reliable connection to the target cell has been established and therefore the chances that the call will be terminated abnormally due to failed handovers are lower. However, by far a bigger advantage comes from the mere fact that simultaneously channels in multiple cells are maintained and the call could only fail if all of the channels are interfered or fade at the same time . Fading and interference in different channels are unrelated and therefore the probability of them taking place at the same moment in all channels is very low. Thus the reliability of the connection becomes higher when the call is in a soft handover. Because in a cellular network the majority of the handovers occur in places of poor coverage, where calls would frequently become unreliable when their channel is interfered or fading, soft handovers bring a significant improvement to the reliability of the calls in these places by making the interference or the fading in a single channel not critical. This advantage comes at the cost of more complex hardware in the phone, which must be capable of processing several channels in parallel. Another price to pay for soft handovers is use of several channels in the network to support just a single call . This reduces the number of remaining free channels and thus reduces the capacity of the network. By adjusting the duration of soft handovers and the size of the areas, in which they occur, the network engineers can balance the benefit of extra call reliability against the price of reduced capacity.
Besides these handover classification categorized as two types such as
1. Vertical handover
2. Horizontal handover
Vertical handoff:
Vertical handover or vertical handoff refers to a network node changing the type of connectivity it uses to access a supporting infrastructure, usually to support node mobility. For example, a suitably equipped laptop might be able to use both a high speed wireless and a cellular technology for Internet access. Wireless LAN connections generally provide higher speeds, while cellular technologies generally provide more ubiquitous coverage. Thus the laptop user might want to use a wireless LAN connection whenever one is available, and to ‘fall over’ to a cellular connection when the wireless LAN is unavailable. Vertical handovers refer to the automatic fallover from one technology to another in order to maintain communication . This is different from a ‘horizontal handover’ between different wireless access points that use the same technology in that a vertical handover involves changing the data link layer technology used to access the network.
Vertical handoffs between WLAN and UMTS (CDMA2000) have attracted a great deal of attention in all the research areas of the 4G wireless network, due to the benefit of utilizing the higher bandwidth and lower cost of WLAN as well as better mobility support and larger coverage of UMTx. Vertical handovers among a range of wired and wireless access technologies including WiMAX can be achieved using which is standardized as IEEE 802.21.
Horizontal handoff:
In this handoff process, the handoff of a mobile terminal takes place between base stations supporting the same network technology. For example, the changeover of signal transmission due to the mobility of the mobile terminal from an IEEE 802.11b base station to a neighboring IEEE 802.11b base station is considered as a horizontal handoff process. Signal strength and channel availability are needed to consider in horizontal handoff
Handover Decision
The decision-making process of handoff may be centralized or decentralized (i.e., the handoff decision may be made at the MS or network). From the decision process point of view, one can find at least three different kinds of handoff decisions.
(a) Network controlled hand-off:
in a network control hand off protocol, the network makes a handoff decision based on the measurement of the MSs and at a number of BSs.Network –controlled hand-off is used in first generation system such as AMPS(Advance mobile protocol system), TACS (total access communication system), and NMT (advanced mobile phone system).
(b) Mobile-Assisted Handoff:
In a mobile-assisted handoff process, the MS makes measurements and the network makes the decision. In the circuit-switched GSM (global system mobile), the BS controller (BSC) is in charge of the radio interface management .
(c) Mobile-Control Handoff:
In mobile-controlled handoff, each MS is completely in control of the handoff process. MS measures the signal strengths from surrounding BSs and interference levels on all channels. A handoff can be initiated if the signal strength of the serving BS is lower than that of another BS by a certain threshold.
Desirable features of handoff
An efficient handoff algorithm can acquire many desirable features. Some of the major desirable features of any handoff algorithm are described bellow:
- Reliability: a handoff algorithm should be reliable all call should be reliable after handoff. Many factor help in determining potential service such signal to interference ratio (SIR), signal to noise ratio (SNR) etc .
2. Seamless: A handoff algorithm should be fast so that the mobile device does not experience service degradation or interruption during the handoff process. Service degradation may be due to a continuous reduction in signal strength or an increase in co-channel interference (CCI).
3. Interference: A handoff algorithm should avoid high interference. The Co-channel and interchannel interferences can degrade the transfer rate of a wireless network. Co-channel interference is caused by devices transmitting on the same channel and on the other hand, interchannel interference is caused by devices transmitting on adjacent channel.
4. Load balance: A handoff algorithm should balance traffic in all cells, whether of the same or different network type. This helps to eliminate the borrowing of channels from the neighboring cells to reduce the probability of new call blocking .
5. Minimizing the no of handoff: The number of handoffs should be minimized in a handoff scenario, because more the number of handoff attempted, the greater the chances that a call will be denied access to a channel, resulting in a higher handoff call dropping probability .
The two prioritization techniques are: guard channels and queuing handover calls The guard channel scheme reserves some fixed or adaptively changing number of channels for handover calls only. The rest of the channels are used by new and handover calls. So the handover calls are better served and forced termination probability is decreased. The cost of such a scheme is an increase in call blocking probability and total carried traffic.
Queuing handover calls is another prioritization scheme. It queues the handover calls when all of the channels are occupied in a BS. When a channel is released, it is assigned to one of the handover calls in the queue . A new call request is assigned a channel if the queue is empty and if there is at least one free channel in the BS. This technique queues new calls to decrease call blocking probability. The time interval between handover initiation and receiver threshold makes it possible to use queuing handover calls. Queuing handover calls can be used either with the guard channel scheme or not .
Software
In this project, we use NS-2.34 software for simulation purpose. Now here given the primary concept about the NS-2.34 software.
NS-2.34: Network Simulator version 2.34
- NS-2.34
- Is a discrete event simulator for networking
- research Simulates at packet level
- Substantial support to simulate many protocols
- Simulate wired and wireless network
- Is primarily Unix based
- NS-2 is the de facto experiment environment in research community
Reason behind using NS-2
- Easy to use friendly simulator
- Well documented easy to understand programming environment
- Well designed software
- Bug free software
- NS 2.34 is not for dummies
Advantage of NS-2.34
1. Open source
2. Supported protocols
3. Supported platforms
4. Modularity
5. Popular
Languages:
NS-2 is implemented by two languages
C++
OTcl: OO + TCL
. C++ is powerful and fast language which is complied
. OTcl is easy to use which is interpreted
OTcl Basics:
- set: Assign a value to a variable
- $x: The value of variable x
- [ … ]: Run command and return result
- [expr …]: Calculate the value of expression
- set x $a: Assign value of a to variable x
- puts …: print out
- proc: Define a procedure
- gets stdin x: Read variable x from stdin
Simulation steps
- Simulation design
- Simulation purposes
- Type of expected results,
- Configuring and Running simulation
- Network configuration
- Nodes, links, traffics, …
- Simulation configuration
- Clock, events, …
- Run (multiple times)
- Post processing=
- Result, analyses, …
NS-2 Internal implementation:
- Discrete event scheduler
- Network topology
- Routing
- Transport
- Application
- Packet Flow
- Packet Format
Simulation and result
The goal for simulation is to test the performance of handover according to the properties of mobile WiMAX in practice. In this chapter, we first implement a very basic scheme is planned with the Network Simulator [25] (version 2.34 with additional WiMAX and mobility packets from NIST project [23, 24]).
Handover Latency with NS2
In the context of ubiquitous connectivity, a mobile station (MS) equipped with an IEEE 802.16 interface is likely to roam across multiple base stations (BS) in order to maintain connectivity. However, as in most mobility scenarios, finding the target BS that best fits the mobility path and application requirements is far from being trivial. The IEEE 802.16e standard supports temporarily suspending the communication between the BS and the MS in order for the mobile to perform channel scanning.
It is preferable for the MS to perform this scanning and obtain a list of neighboring BSs before it is ready to perform a handover because channel scanning can be a relatively time consuming activity. During this scanning period, both upstream and downstream packets originating at the
mobile and destined to it are buffered at the MS and BS, respectively.
The IEEE 802.16 standard defines the mechanisms for a user equipment to connect to a BS. Figure 5.11 shows the so-called network entry phase, which consists of both synchronization and association operations. During the synchronization step, the MS received broadcast messages, which are sent by the BS and contain information about how and when to access the channel. The downlink (DL_MAP) and uplink (UL_MAP) messages contain burst allocation for each frame. The downlink channel descriptor (DCD) and uplink channel descriptor (UCD) contain transmission parameters of each burst.
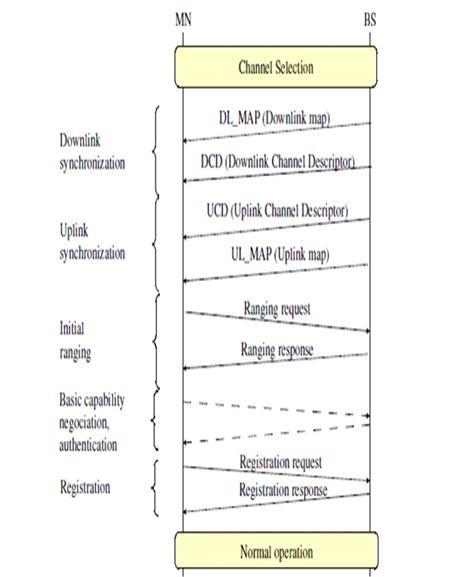
Fig : Network entry in the mobile wi-max
In order to reduce the period of channel scanning time, the IEEE 802.16e defines the mechanisms related to BS communication and channel scanning in order to facilitate neighbor discovery and handovers. Regarding BS communication, the assumption in IEEE 802.16e is that neighboring BSs exchange DCD and UCD messages over the backbone. The information is then embedded in messages sent periodically by the serving BS to the MSs. This allows an MS to acquire channel information prior to any scanning. Mechanisms related to channel scanning are in the form of requests by the MS seeking to maintain information about neighboring BSs
Simulation Scenario
The all-in-one package of the outdated NS-2 did not include support for mobile WiMAX and therefore additional components are required. ,so we useNS-2.34 to achieve simulations of mobile scenarios,whice is convenient than other version.
There is an example scenario in the provided modules, which is taken as a basis for our simulations. The basic idea of a MS traveling through the coverage areas of two 802.16e BSs is shown in Figure 5.13. Each BSs’ coverage areas have a radius of 1 km. The channel scanning interval is set up to 2 frames and the contention probability is 5 times per frame.