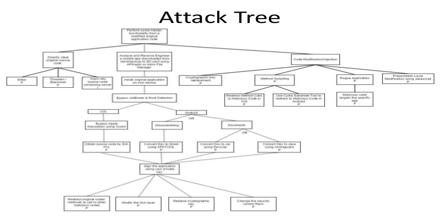
Attack Tree is a good way to move threat scenarios from the realm of art form to science. It can be used to map out the various components of a threat scenario and organize them into a more easily understood structure. It’s provide a formal, methodical way of describing the security of systems, based on varying attacks. Basically, you represent attacks against a system in a tree structure, with the goal as the root node and different ways of achieving that goal as leaf nodes. Attack Tree also provide a systematic way to compare existing Threat sources with Vulnerabilities to identify the most likely exploits that Threats would use.
Attack Tree