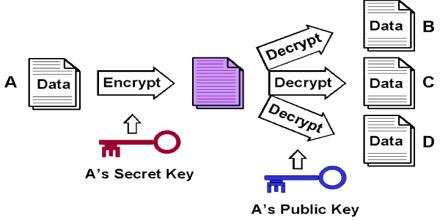
Public key Cryptography is uses public and private keys to encrypt and decrypt data. The keys are simply large numbers that have been paired together but are not identical. It is also used in software programs, such as browsers, which need to establish a secure connection over an insecure network like the internet or need to validate a digital signature. This systems often rely on cryptographic algorithms based on mathematical problems that currently admit no efficient solution—particularly those inherent in certain integer factorization, discrete logarithm, and elliptic curve relationships. Public Key Cryptography finds application in the information technology security discipline, information security.
Public key Cryptography