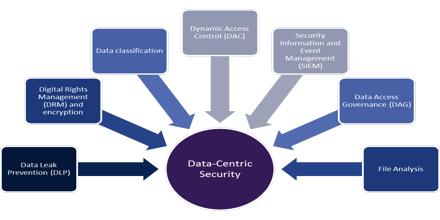
Data Centric Security solution targeted at directly protecting the data, versus the devices at the endpoints of the organization, will add additional fortification to security measures currently in place. It focuses on protecting data rather than protecting the network where the data lives. In the ideal data-centric model, sensitive date is encrypted and only authorized users can get the cryptographic key needed to decrypt it. To unauthorized users, data looks like a bunch of random bits, and because they can’t get the key needed to turn these random bits into useful information, the data isn’t useful to them. Data Centric Security is evolving rapidly as enterprises increasingly rely on digital information to run their business and big data projects become mainstream.
Data Centric Security